|
Voiced by Amazon Polly |
Introduction
In today’s cloud-native era, applications are distributed across containers and clusters, serving thousands of users simultaneously. With this scale comes the need for centralized identity and access management (IAM). Managing authentication and authorization at the application level becomes complex and error-prone.
This is where Keycloak shines.
Keycloak is an open-source Identity and Access Management solution from Red Hat. It provides:
- Single Sign-On (SSO)
- Identity brokering and social logins (Google, GitHub, etc.)
- User federation (LDAP, Active Directory)
- Fine-grained role-based access control (RBAC)
- OAuth2.0 and OpenID Connect for API security
When deployed on Kubernetes (K8s), Keycloak offers a scalable, cloud-native authentication layer that integrates seamlessly with microservices. Pairing it with Amazon RDS for the database ensures durability, high availability, and simplified database management.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
Why Keycloak with Kubernetes?
Kubernetes provides container orchestration, scaling, and resilience. However, it doesn’t natively solve user identity management. Keycloak fills this gap by acting as a centralized authentication hub.
Benefits:
- Centralized Authentication – One identity provider for multiple apps and services.
- Microservices Security – Secure APIs with JWT tokens issued by Keycloak.
- Seamless User Experience – Enable Single Sign-On (SSO).
- Scalability – Kubernetes ensures Keycloak can handle increasing load.
- Durable Storage – Amazon RDS ensures the database backend is always available and resilient.
Common Use Cases
- Multi-App Authentication: Allowing users to log in once and access multiple apps.
- API Gateway Security: Protecting microservices using OAuth2/OpenID Connect tokens.
- Enterprise Integration: Connecting to LDAP/AD for employee authentication.
- Cloud-Native IAM: Centralized identity for Kubernetes-hosted applications.
Step-by-Step Deployment: Keycloak on Kubernetes with Amazon RDS
Step 1: Prerequisites
- A Kubernetes cluster (Amazon EKS/AKS/GKE/Minikube).
- kubectl and (optionally) helm installed.
- An Amazon RDS MariaDB/MySQL instance created, with:
- Database: dev_keycloak
- Username and Password for Keycloak.
- Security group allowing access from K8s worker nodes
Step 2: Create a Namespace
|
1 |
kubectl create namespace keycloak |
Step 3: Store Secrets in Kubernetes
Instead of exposing credentials directly in YAML, use a Secret, and follow best practices as below:
Use AWS Secrets Manager for production environments.
Enable automatic secret rotation
Use AWS IAM roles for service accounts (IRSA) for secure access
Never commit secrets to version control
Step 4: Deploy Keycloak with Amazon RDS
Here’s the Deployment manifest:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 |
apiVersion: apps/v1 kind: Deployment metadata: name: keycloak namespace: keycloak labels: app: keycloak spec: replicas: 1 selector: matchLabels: app: keycloak template: metadata: labels: app: keycloak spec: containers: - name: keycloak image: quay.io/keycloak/keycloak:26.0 args: ["start"] ports: - name: http containerPort: 8080 - name: https containerPort: 8443 env: - name: KC_DB value: "mariadb" - name: KC_DB_USERNAME valueFrom: secretKeyRef: name: keycloak-secrets key: db-username - name: KC_DB_PASSWORD valueFrom: secretKeyRef: name: keycloak-secrets key: db-password - name: KC_DB_URL value: "jdbc:mariadb://rds-hwbefjvvh/wheeb " - name: KC_HOSTNAME value: "hostname.net" - name: KEYCLOAK_ADMIN valueFrom: secretKeyRef: name: keycloak-secrets key: admin-username - name: KEYCLOAK_ADMIN_PASSWORD valueFrom: secretKeyRef: name: keycloak-secrets key: admin-password - name: KC_HOSTNAME_STRICT value: "true" - name: KC_HTTP_ENABLED value: "true" - name: KC_PROXY_HEADERS value: "xforwarded" - name: KC_HOSTNAME_STRICT_HTTPS value: "true" - name: KC_DB_POOL_INITIAL_SIZE value: "5" - name: KC_DB_POOL_MIN_SIZE value: "5" - name: KC_DB_POOL_MAX_SIZE value: "20" - name: KC_TRANSACTION_XA_ENABLED value: "false" - name: KC_PROXY value: "edge" |
![]()
Step 5: Expose Keycloak Service
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
apiVersion: v1 kind: Service metadata: name: keycloak namespace: keycloak spec: type: ClusterIP ports: - name: http port: 8080 targetPort: 8080 - name: https port: 8443 targetPort: 8443 selector: app: keycloak |
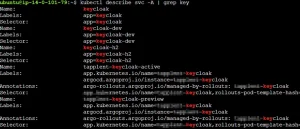
Step 6: Configure Ingress (with ALB on AWS)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: keycloak-ingress namespace: keycloak annotations: kubernetes.io/ingress.class: alb alb.ingress.kubernetes.io/scheme: internet-facing alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80}, {"HTTPS":443}]' alb.ingress.kubernetes.io/target-type: ip spec: rules: - host: hostname http: paths: - path: / pathType: Prefix backend: service: name: keycloak port: number: 8080 |
Make sure DNS points to the ALB.
![]()
Step 7: Validate Deployment
- Check pods:
kubectl get pods -n keycloak
- Logs:
kubectl logs -n keycloak deploy/keycloak
- Access in browser:
https://hostname.net
Login with admin / and password.
Conclusion
Keycloak provides an open-source way to handle authentication and authorization across modern applications. Deploying it on Kubernetes ensures scalability and resilience, while using Amazon RDS as the backend database guarantees durability and reliability.
Drop a query if you have any questions regarding Keycloak and we will get back to you quickly.
Empowering organizations to become ‘data driven’ enterprises with our Cloud experts.
- Reduced infrastructure costs
- Timely data-driven decisions
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. Can Keycloak replace Auth0 or Okta?
ANS: – Yes. Keycloak is a free, open-source alternative to SaaS identity providers like Auth0/Okta. The difference is that you manage the infrastructure, scaling, and upgrades.
2. Why use Amazon RDS instead of the default H2 database?
ANS: – H2 is only for development. For production, Keycloak needs a persistent, reliable database. Amazon RDS ensures durability, high availability, and automated backups.

WRITTEN BY Deepika N
Deepika N works as a Senior Research Associate - DevOps and holds a Master’s degree in Computer Applications. She is passionate about DevOps and related technologies. Deepika has strong expertise in AWS and Azure DevOps, Kubernetes (EKS), Terraform, and CI/CD pipelines. She is proficient in infrastructure as code, automation, monitoring, security enforcement, and multi-cloud deployment strategies. Skilled in version control, infrastructure documentation, cloud-native technologies, and managing production workloads, container platforms, and DevSecOps practices, Deepika brings comprehensive hands-on experience to her role.


 Login
Login


 September 17, 2025
September 17, 2025 PREV
PREV











Comments