|
Voiced by Amazon Polly |
Introduction
AWS IAM identity center is the successor to AWS single sign-on and a dedicated service to authenticate and authorize your workforce to Interact with AWS services. It helps centrally manage the account and user permissions along with common groups for users having similar jobs and assigns users access to multiple accounts in an organizational structure. It also assigns usernames, passwords, and multi-factor authentication so that users can gain access to multiple accounts centrally.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
Use Case
Day-to-Day Task used by a Sys-Ops Engineer
Identity Management
- Users: Users can be created here; optionally, you can attach permissions if needed. This will send an invite to their respective email ID, and users can set up their password. Users can also set up MFA if it’s mandatory as per their organization’s guard rails setup in their control tower.

2. Groups: Groups are the stacks of permissions and accounts allotted. If a user is a part of the group, he will have access to the accounts and the permission sets attached. A user can be part of a group or optionally cannot if used as a guest user.

3. Settings: Here you find settings related to the multi-factor authentication, email OTP, session duration, password policy.

4. AWS accounts: Here, you can view your organizational level structure. You can directly start attaching permissions by choosing an account, users/groups, and permission sets.
5. Permission sets: Permission is one of the most important parts and features of the IAM identity center. You can create gradual permissions here, including AWS managed or custom JSON policies.

Steps for User creation and Assign Permissions
Let’s look into how we can create a user and assign a permission set in the console.
Navigate to the IAM identity center, then User, and click on add a user.
You need to specify a unique username in your organization and email ID where the user will get an invitation to set up the password and the MFA.

Now we will create a permission set that has to be assigned to a user.
Navigate to Permissions sets in the left pane.

You can create a predefined or custom permission set here.

You can add AWS managed policies, customer managed, inline policies to fine grain and customize each permission set for separate job roles.

Here we have chosen AWS managed “S3 full access” for the demo.
Next, give a name to the set, a description, and session duration, review and create.
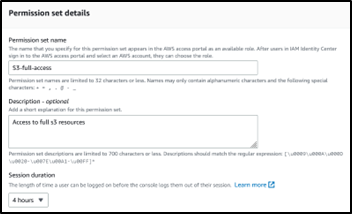
To assign this permission, choose the AWS account you want to allocate and click on Assign users.

Select your users and attach the permission set to the same.

Review and Submit.
Now you will be able to see the user allocated with the AWS account you selected under the organizations with the required permission.
Application support for the IAM Identity center
With the IAM identity center, you can easily integrate a pre-existing identity source such as an active directory, Azure AD, and more. At a particular time, you can add only one identity provider. You can use SCIM to synchronize the identity data, such as Users/groups from another IDP. If you want to connect an on-premise active directory, you can use AD connect from AWS.
Suppose your application can be integrated to AWS IDC with a protocol such as SAML 2.0. In that case, you can connect by navigating to the application panel, configuring the new application, and choosing custom SAML 2.0.
To establish a SAML trust connection with your cloud application provider, IAM Identity Center utilizes certificates. An IAM Identity Center certificate used with the application throughout the setup process is automatically produced when you add an application to IAM Identity Center. This automatically created IAM Identity Center certificate has a five-year expiration date by default.
Region and data
All of the information you configure in the IAM Identity Center is saved in the Region where it was defined when you initially enabled IAM Identity Center. These details include user assignments to Amazon account apps, directory setups, permission sets, and application instances.
An AWS Organization can support just one AWS Region at once. You must first erase your current IAM Identity Center setup to enable AM Identity Center in a new Region.
Security and Compliance
The International Organization for Standardization (ISO), System and Organization Controls (SOC) 1, 2, and 3, Esquea Nacional de Seguridad (ENS) High, the Financial Market Supervisory Authority (FINMA), International Standard on Assurance Engagements (ISAE) 3000 Type 2 Report requirements, and Multi-Tier Cloud Security are among the security standards and compliance requirements that IAM Identity Center supports. The service has a PROTECTED level Information Security Registered Assessors Program (IRAP) assessment.
The ability to centrally audit IAM Identity Center activities is possible because all administrative and multi-account access activity is documented in Amazon CloudTrail. You may view activities like sign-in attempts, application assignments, and directory integration modifications through CloudTrail.
Conclusion
IAM identity center helps in centralizing your management user identities and permissions. Use the service for easy and fast accessibility to IAM management. Users and groups permissions set in combination can provide appropriate access to different job roles. Protect your access to AWS resources with SSO and MFA and meet the required compliance. As a system manager in AWS, one must have in-depth knowledge of the IAM identity center, the successor to Single Sign On.
Upskill Your Teams with Enterprise-Ready Tech Training Programs
- Team-wide Customizable Programs
- Measurable Business Outcomes
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. Is there any cost incurred for using IAM Identity Center?
ANS: – There is no additional cost associated with IAM Identity Center.
2. Can we add multi-factor authentication for users signing through the IAM identity center?
ANS: – Yes, you can enable MFA through settings, and users will then be prompted to register a device for MFA for secure logging.
3. Who should be the stakeholders for access to IAM Identity Center permissions and user creation?
ANS: – IT administrators who manage users in the organization and provide access to multiple accounts and permissions based on different job roles for other employees should have access to the service.

WRITTEN BY Akshay Mishra
Akshay Mishra works as a Subject Matter Expert at CloudThat. He is a Cloud Infrastructure & DevOps Expert and AWS Certified. Akshay is experienced in designing, securing, and managing scalable cloud infrastructure on AWS. Proven track record working with government, pharmaceutical, and financial clients in roles such as Cloud Engineer, Associate Solutions Architect, and DevOps Engineer. He is skilled in AWS infrastructure, CI/CD, Terraform, and cloud security, with certification in AWS Security – Specialty.


 Login
Login


 March 23, 2023
March 23, 2023 PREV
PREV











Comments