|
Voiced by Amazon Polly |
In the current digital-centric environment, Office 365 Security is a primary concern for companies of every scale. Still, numerous companies primarily concentrate on creating policies, believing that documentation alone will safeguard their data and users. The reality is that proper protection demands a robust architectural approach- one that goes far beyond paperwork, weaving security and compliance into the very fabric of your technology and daily operations. This blog explores why building security architecture matters, how compliance training supports it and actionable steps to put these principles into practice, with insights relevant to course-specific training and solutions.
Freedom Month Sale — Upgrade Your Skills, Save Big!
- Up to 80% OFF AWS Courses
- Up to 30% OFF Microsoft Certs
- Ends August 31
Why Security Architecture Matters
Regarding Office 365, let us define the security architecture. Policies are crucial; they are one part of a much larger framework, as they establish norms, guidelines and expectations. The design, execution and integration of people, procedures and technology that cooperate to safeguard data, guarantee compliance and preserve business continuity are all included in security architecture.
In simple words, architecture is more than just recording intents; it’s about creating solid foundations that support your security objectives. An architectural approach guarantees that the multi-factor authentication (MFA) system is installed correctly, monitored and routinely tested.
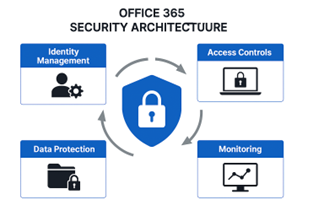
Fig 1: Office 365 Security Architecture
Policies vs. Architecture: The Critical Difference
The “what” and “why” of your organization are defined by its policies. The “how”- the operational, technological and practical fulfilment of those goals- is architecture. A solely policy-based strategy could result in significant gaps. For instance, Office 365’s default options typically diverge from best practices, leaving organizations at risk for issues like data breaches and illegal access.
A robust security architecture for Office 365 should include:
- Identity and Access Management: Enforce strong authentication (MFA), conditional access and least-privilege principles.
- Threat Protection: Deploy Microsoft Defender for Office 365, Safe Links and Safe Attachments to guard against phishing and malware.
- Data Protection: Use encryption, Data Loss Prevention (DLP) and sensitivity labels to safeguard sensitive information.
- Monitoring and Response: Implement continuous monitoring, audit logs and incident response plans.
The Role of Compliance Training
If people aren’t trained to use it properly, even the best architecture can fail. IT teams, end users and decision-makers are guaranteed to comprehend not only the policies but also the architecture and instruments that uphold them, thanks to compliance training. Training will highlight:
- Continuous Learning: Attending frequent updates and refresher courses to stay abreast of changing regulations and evolving risks.
- Practical labs: Real-world situations for setting up security measures, handling problems and overseeing legal obligations.
- Understanding the Shared Responsibility Model: Being aware of what Microsoft secures and what your company needs to secure
Office 365 security courses, such as MS-500: Microsoft 365 Security Administration and MS-4002: Prepare security and compliance to support Microsoft 365 Copilot, offer hands-on, scenario-based learning to bridge the gap between policy and practice.

Fig 2: Empowering employees through compliance training.
Best Approaches for Building Security Architecture
Organizations ought to consider the following when switching from policy to architecture:
- Analyse and make comparisons
Use Microsoft Purview Compliance Manager to begin with a compliance assessment. This tool compares your posture with global standards, analyzes your configuration and provides a compliance score.
- Provide Access Least-Privilege
Ensure that users only have the access they need at the appropriate time by using Entra Privileged Identity Management (PIM).
- Enable multi-factor authentication.
Arguably, the best defences against credential compromise are MFA. Ensure that all administrators and users have it enabled.
- Disable Legacy Authentication
Since MFA is not enabled, legacy protocols such as IMAP and POP3 are often misused. To get rid of a significant attack point, disable it.
- Monitor and Respond
Conduct constant surveillance with Microsoft Defender and set up automated notifications for suspicious activities. Analyze incident reports and audit logs at regular intervals.
- Train Continuously
Every employee must receive continuous compliance training. Training that incorporates a blended learning approach, integrating labs, instructor-led workshops and self-paced courses, ensures that skills are continually updated and remain effective over time.
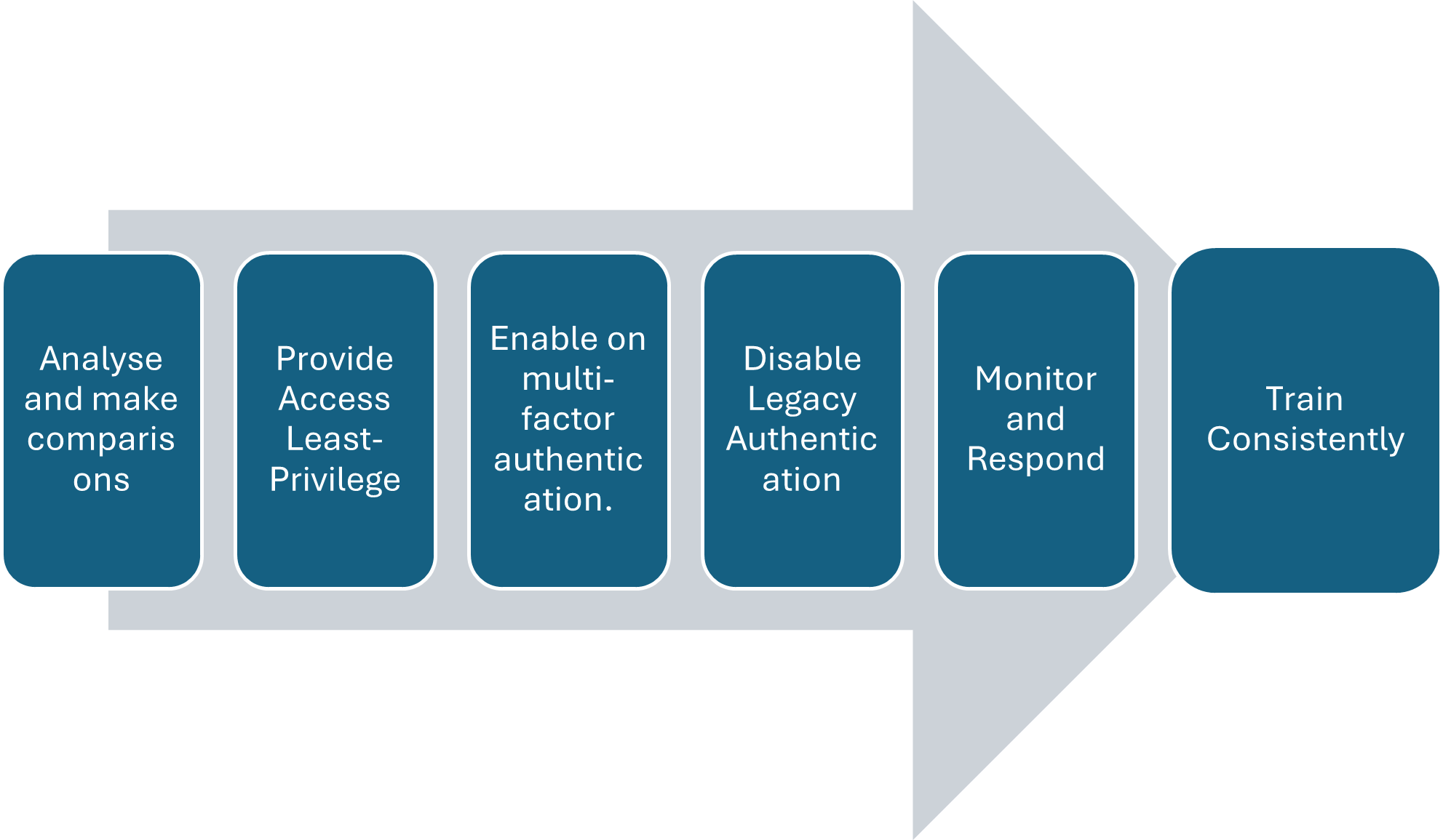
Fig 3: The best approach for building a security architecture.
Integrating Security and Compliance:
The training courses in the field of Cybersecurity are aimed at supporting organizations in developing and maintaining a reliable security architecture, along with assisting them in comprehending rules. With a focus on practical expertise, real-life scenarios and relevant content, organizations enable IT workers to:
- Secure user access and identities
- Protect data with DLP and encryption
- Respond to threats with Defender for Office 365
- Maintain compliance with evolving regulations
Explore more about Microsoft’s Cybersecurity Certification Training courses to build a future-ready security posture.
Turning Policy Into Practical Security Architecture
Having the appropriate policies is not enough to create a safe and compliant Office 365 environment; one must additionally ensure that everyone knows how to utilize it and incorporate those policies into a strong, flexible and effective architecture. Organizations can safeguard their data, comply with regulatory standards and ensure business continuity in a fast- evolving digital landscape by emphasizing architecture, implementing regular training and leveraging specialized resources in the area of cybersecurity.
Freedom Month Sale — Discounts That Set You Free!
- Up to 80% OFF AWS Courses
- Up to 30% OFF Microsoft Certs
- Ends August 31
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.

WRITTEN BY Neharika
Neharika is a Microsoft Certified Trainer at CloudThat. She is an enthusiastic and passionate trainer and an empathic observer towards the trending technologies with demonstrated skill in delivering corporate training on Microsoft Fabric, Data Analysis in Microsoft Power BI, Data Visualization using Tableau and Advance Excel with Copilot. She has 8 years of experience in training Industry and has delivered several trainings, seminars and webinars online as well as offline. She has trained 3500+ professionals and conducted 500+ trainings so far. She has delivered training for Microsoft and several corporate clients. She has won the MCT QUALITY AWARD and was recognized as one of the Top 100 MCT across the Globe for the year 2024-2025.


 Login
Login


 December 16, 2025
December 16, 2025 PREV
PREV











Comments