|
Voiced by Amazon Polly |
Introduction
Containerization has transformed the way we build, ship, and deploy applications. Docker, one of the most widely used container platforms, has made it easier than ever to package applications into lightweight, portable units. While Docker Hub provides a convenient public registry for storing and sharing container images, many organizations and developers prefer more control over their image distribution. This is where a Docker private repository comes into play.
Hosting a private Docker registry lets you manage, secure, and store your container images internally. Whether you’re building proprietary software, working in a restricted network environment, or aiming to improve security and performance, setting up a private registry is smart.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
Why Do You Need a Private Docker Repository?
- Security and Compliance
When working with proprietary code, sensitive data, or regulated environments, you don’t want your images accessible through a public platform, even if marked private. A self-hosted registry controls who can access your images, how they’re stored, and where they’re deployed.
- Avoiding Docker Hub Rate Limits
In late 2020, Docker Hub began enforcing rate limits for anonymous and free-tier users. This can impact your CI/CD pipelines if you pull many images frequently. A private registry helps eliminate that bottleneck and provides consistent access to your required images.
- Performance Optimization
Serving container images from an internal network greatly improves performance. It reduces latency and download times compared to pulling from external services, especially in enterprise environments where dozens or hundreds of microservices are deployed continuously.
- Customization and Flexibility
Self-hosting allows you to customize storage, implement access control mechanisms, integrate with LDAP or OAuth for user management, and monitor usage per your organizational needs.
Real-World Use Cases
- Software Companies: Internal tools and pre-release builds often must be kept private. A local registry ensures only authorized developers or testers have access, helping maintain confidentiality during early development stages.
- Government and Defense Organizations: Projects that involve sensitive data, national security, or classified systems require complete isolation. Using a private registry allows these entities to comply with strict regulatory frameworks without relying on third-party services.
- Enterprises with Large DevOps Teams: In complex organizations with hundreds of microservices and distributed teams, having an internal image repository reduces image pull time, ensures availability during deployments, and integrates tightly with internal CI/CD workflows.
- Offline or Air-Gapped Environments: In locations with restricted internet access (such as manufacturing plants, offshore rigs, or military operations), a private registry allows containerized applications to be deployed and updated locally without any external dependency
- Educational Institutions and Labs: Schools, universities, and research labs can use private registries to share containers for coursework, simulations, or experiments, without exposing them to the public.
- Managed Hosting Providers: Service providers offering managed infrastructure can isolate client environments using private registries, ensuring each client’s images remain secure and accessible only to their systems
Setting Up a Docker Private Repository
Step 1: Create a VM with Ubuntu 20.04 server
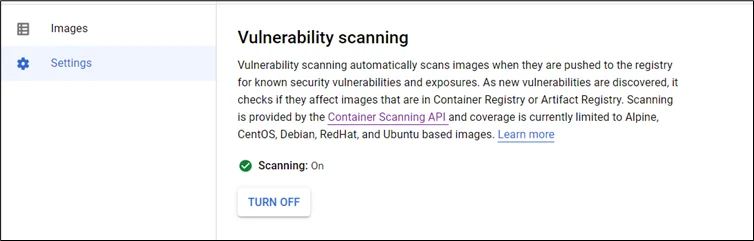
Steps to enable GCP API (Container Scanning API):
- Search APIs and Services in the search bar
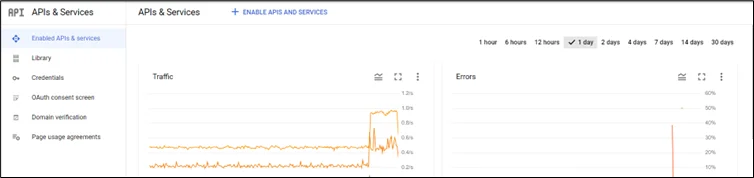
2. Go to ENABLE APIS AND SERVICES
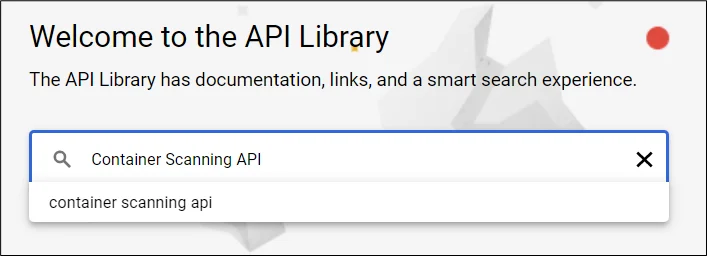
3. In the search bar, enter Container Scanning API
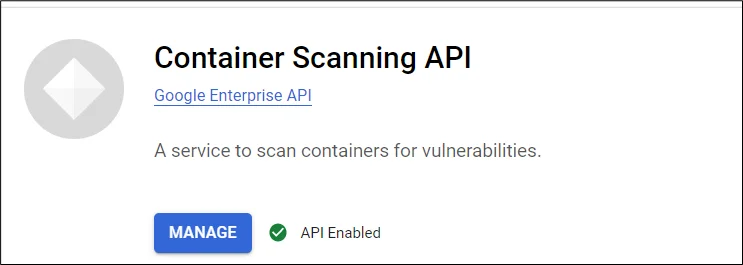
4. Enable the API by clicking on the Enable API
5. Go to the container registry and under settings, turn on scanning on
Step 2: Enabling API through GCP CLI
|
1 2 3 |
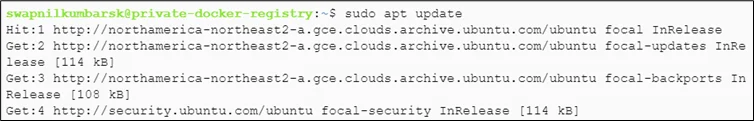
# gcloud services enable containerregistry.googleapis.com Install Docker #sudo apt update |
|
1 |
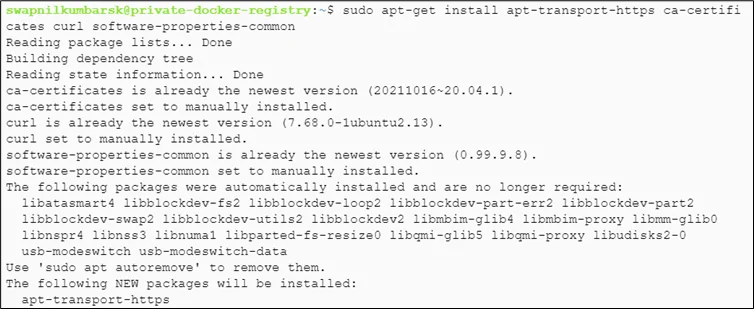
#sudo apt-get install apt-transport-https ca-certificates curl software-properties-common -y |
|
1 |
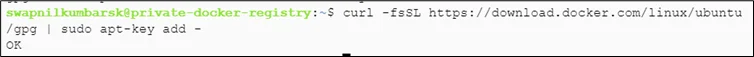
#curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add – |
|
1 |
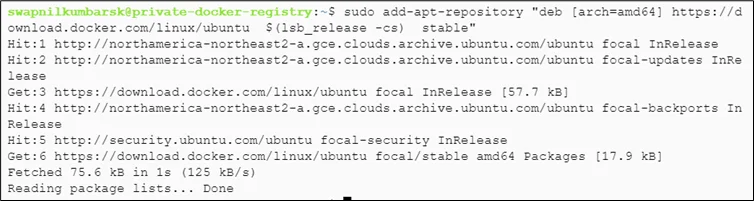
#sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable" |
|
1 |
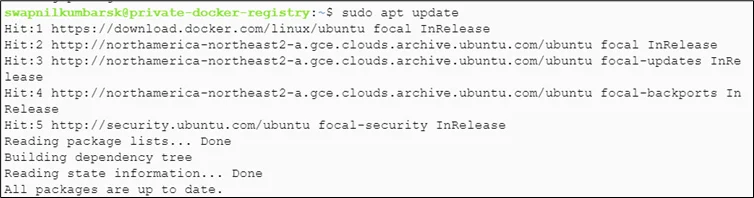
#sudo apt update |
|
1 |
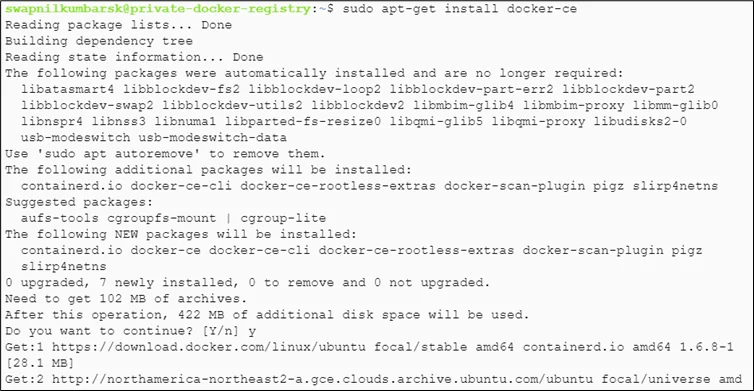
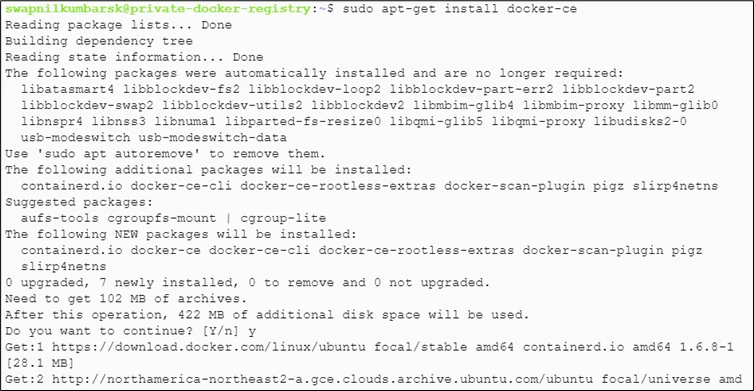
#sudo apt-get install docker-ce -y |
|
1 |
#sudo usermod -aG docker $USER |
![]()
|
1 |
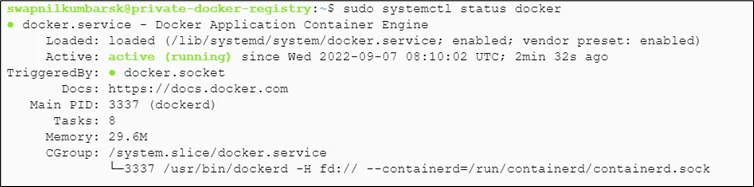
#sudo systemctl status docker |
Step 3: Install Docker-compose
|
1 |
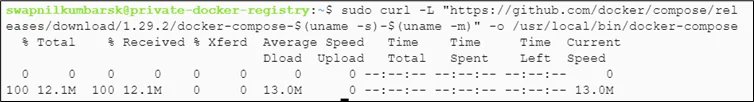
#sudo curl -L "https://github.com/docker/compose/releases/download/1.29.2/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose |
|
1 |
#sudo chmod +x /usr/local/bin/docker-compose |
![]()
|
1 |
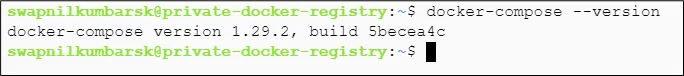
#docker-compose –version |
|
1 |
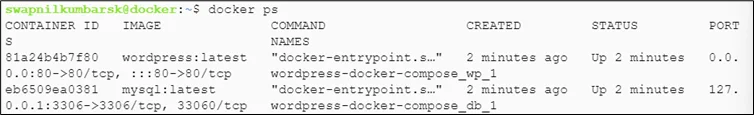
#docker ps |
Here in this VM, the WordPress application is running on a Docker container
|
1 |
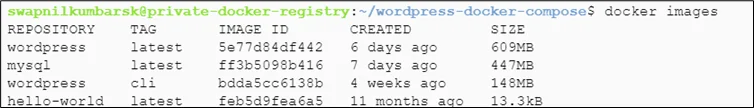
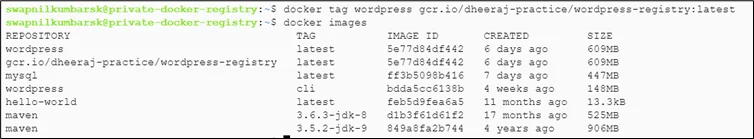
#docker images |
Copy the JSON keyfile from the service account, check with all the permissions
|
1 |
#vi keyfile.json |
Paste the content of the file downloaded and save it.
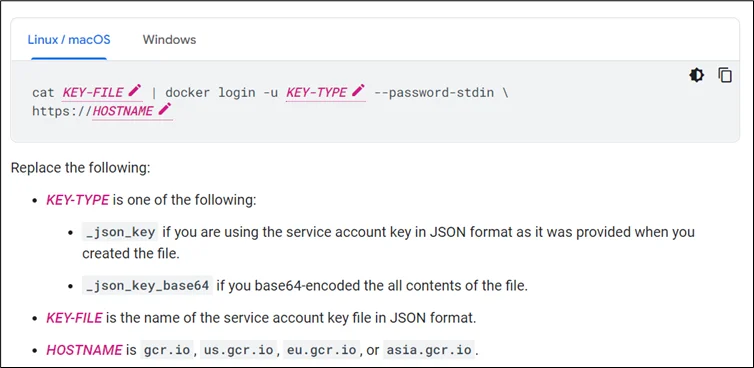
Step 4: Login with the service account
|
1 |
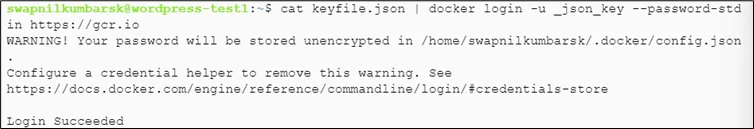
# cat keyfile.json | docker login -u _json_key --password-stdin https://gcr.io |
|
1 |
#docker tag wordpress gcr.io/dheeraj-practice/wordpress-registry:latest |
|
1 |
#docker push gcr.io/dheeraj-practice/wordpress-registry:latest |
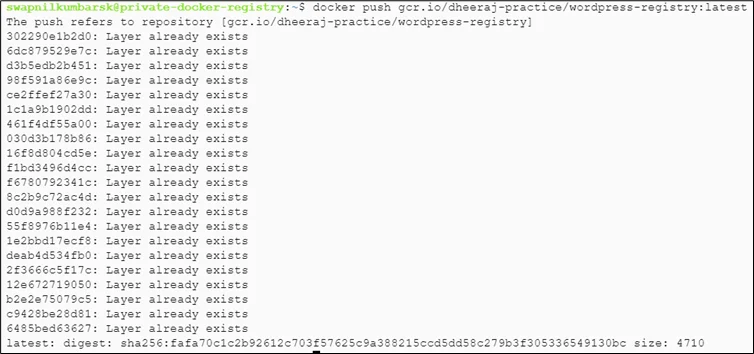
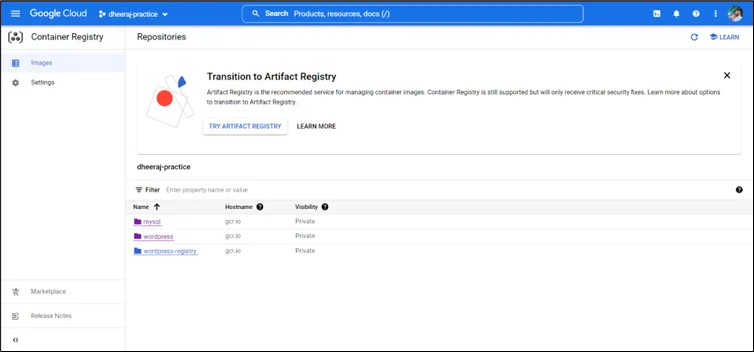
Step 5: Check in GCR for the pushed file.
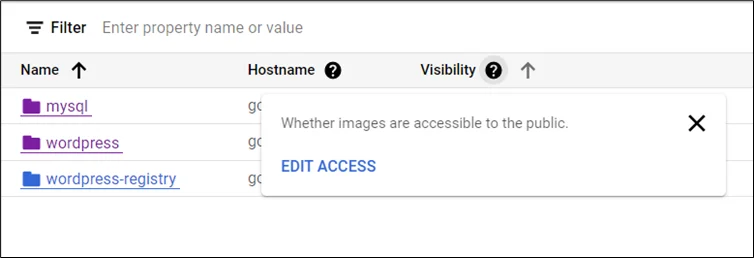
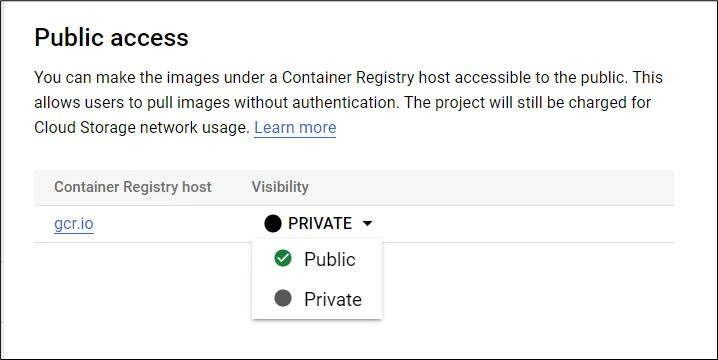
Visibility can be changed to private and public by editing.
Conclusion
A private Docker repository is a powerful asset for teams and organizations prioritizing security, performance, and control. Whether safeguarding proprietary applications, optimizing your CI/CD workflows, or operating in isolated environments, hosting your own registry ensures that your container infrastructure remains efficient, scalable, and secure.
Drop a query if you have any questions regarding Docker and we will get back to you quickly.
Empowering organizations to become ‘data driven’ enterprises with our Cloud experts.
- Reduced infrastructure costs
- Timely data-driven decisions
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. How secure is a private Docker registry?
ANS: – It can be very secure if configured correctly. Use HTTPS, enable authentication (e.g., basic auth or LDAP), and restrict access at the network level.
2. Can I access my registry from other machines?
ANS: – Yes, but if using HTTP (not recommended), client machines must allow insecure registries. With HTTPS, ensure valid certificates are in place.
3. How do I clean up old images?
ANS: – Enable deletion in the registry config and run garbage collection to remove unreferenced layers. This helps reclaim disk space.

WRITTEN BY Swapnil Kumbar
Swapnil Kumbar is a Senior Research Associate at CloudThat with over 2.5 years of experience in DevOps. He specializes in AWS, Kubernetes, automation, and cloud-native technologies. Passionate about innovation and research, Swapnil focuses on building scalable infrastructure, optimizing deployments, and exploring emerging tools. In his free time, he actively contributes to knowledge sharing and community learning initiatives.


 Login
Login


 August 26, 2025
August 26, 2025 PREV
PREV











Comments