|
Voiced by Amazon Polly |
Introduction
The Domain Name System (DNS) is a fundamental part of the Internet infrastructure, translating user-friendly domain names into machine-readable IP addresses. When running services on Google Cloud Platform (GCP), managing DNS efficiently and securely is crucial. GCP Cloud DNS offers a high-availability, scalable, and managed DNS service designed for cloud-native applications and enterprise workloads.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
GCP Cloud DNS
Cloud DNS is a fast, reliable, cost-effective domain name service that GCP provides. It lets users publish and manage DNS records using GCP’s global infrastructure.
- Fully managed and available as part of GCP’s network services
- Supports both public and private DNS zones
- Built on Google’s global Anycast network for low-latency resolution
- Offers integration with services like GKE, Cloud Load Balancing, and Cloud Armor
How It Works?
GCP Cloud DNS functions like any other DNS service but with cloud-native enhancements:
- Managed Zones: You define zones for your domain, either public (internet-facing) or private (internal VPC).
- Record Sets: Within each zone, you create resource records like A, CNAME, MX, TXT, etc.
- Resolution: When a DNS query is made, Cloud DNS resolves it using Google’s global DNS infrastructure.
- Integration: Easily integrates with GCP services, e.g., Kubernetes ExternalDNS can automatically create DNS records for services.
Key Benefits
- Global Performance: Uses Google’s Anycast DNS servers to provide fast query responses worldwide.
- High Availability: Redundant infrastructure ensures DNS services are always available.
- Scalable: Supports millions of DNS queries per second without performance degradation.
- Secure:
- Integrated with IAM for role-based access control
- Supports DNSSEC for protection against spoofing and cache poisoning
- Automation Ready: Manage DNS via API, CLI (gcloud), Terraform, or YAML scripts.
- Seamless GCP Integration: Works smoothly with load balancers, Kubernetes, and App Engine.
Common Use Cases
- Website Hosting: Point domains like com to your web app hosted in GCP or elsewhere.
- Internal Service Discovery: Use private DNS zones to resolve services inside your VPC.
- Hybrid Cloud or Multi-Cloud Networking: Centralize DNS management while supporting services spread across environments.
- Dynamic DNS with GKE: Automate DNS updates for pods and services using ExternalDNS.
- Load Balanced Applications: Combine with GCP load balancers for DNS-level traffic distribution.
Key Considerations Before Using Cloud DNS
Before deploying Cloud DNS, keep these factors in mind:
- Public vs. Private Zones: Understand which zone type suits your use case (public for websites, private for internal networking).
- Security:
- Enable DNSSEC for public zones
- Use IAM to limit who can change records
- Automation Strategy:
- Choose Terraform or ExternalDNS for repeatable, consistent deployments
- TTL Settings:
- Lower TTLs for fast record propagation (with higher DNS traffic)
- Higher TTLs for stable records to reduce query load
- Monitoring:
- Use Cloud Logging and Cloud Monitoring to audit and observe DNS usage
- Pricing:
- Understand the cost structure (charged per zone and per million queries)
How to Set Up Cloud DNS – Overview
- Create a Managed Zone:
- Navigate to Cloud DNS > Create Zone
- Choose type: Public or Private
- Enter a DNS name like com.
- Add DNS Records:
- Use Console, gcloud CLI, or Terraform
- Add A, CNAME, TXT, or MX records as needed
- Integrate with GCP Services:
- Link with Cloud Load Balancers
- Use ExternalDNS for dynamic DNS updates from GKE
- Apply IAM policies for access control
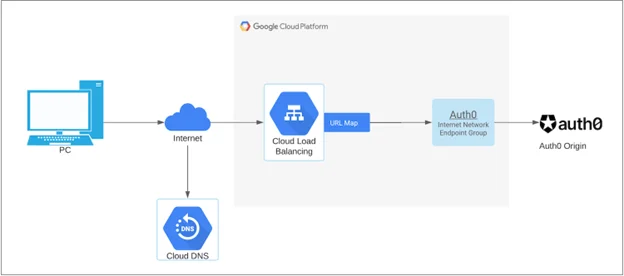
Fig 1. Configure Google Cloud Platform with Load Balancing as a Reverse Proxy
Security and Access Management
- Enable DNSSEC to secure public zones from spoofing and tampering.
- Use Cloud IAM roles like:
- admin – full access
- editor – modify zones/records
- viewer – read-only
- Integrate with Cloud Audit Logs for visibility into all DNS changes.
Monitoring and Troubleshooting
Use GCP tools to track and debug DNS activity:
- Cloud Logging:
- Logs zone changes and DNS queries (if enabled)
- Cloud Monitoring:
- Set alerts for query failures or spikes
- CLI Tools:
- Use dig, nslookup, or gcloud dns to debug DNS resolution issues
Best Practices
- Use Terraform or automation tools for consistent DNS management
- Enable DNSSEC for production public domains
- Use Private DNS zones for VPC-internal services
- Apply least privilege IAM roles
- Maintain monitoring and logging for DNS operations
- Keep TTL values optimized for your infrastructure’s needs
Conclusion
By understanding how it works, implementing it with best practices, and leveraging automation tools, you can simplify DNS management while boosting reliability and control across your entire cloud infrastructure.
Drop a query if you have any questions regarding GCP Cloud DNS and we will get back to you quickly.
Empowering organizations to become ‘data driven’ enterprises with our Cloud experts.
- Reduced infrastructure costs
- Timely data-driven decisions
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. What is the difference between public and private DNS zones in GCP Cloud DNS?
ANS: –
- Public DNS zones manage domain names accessible from the internet (e.g., com).
- Private DNS zones are used for internal domain resolution within a GCP Virtual Private Cloud (VPC). These are not accessible from the public internet and are ideal for internal services and microservices communication.
2. Can I automate Cloud DNS configuration using tools like Terraform?
ANS: – Yes, Terraform is fully supported for GCP Cloud DNS. You can define zones, record sets, and manage lifecycle changes through infrastructure-as-code (IaC). This approach ensures repeatability and version control and reduces manual configuration errors.

WRITTEN BY Vinay Lanjewar
Vinay specializes in designing and implementing scalable data pipelines and end-to-end data solutions on the AWS Cloud. Skilled in technologies such as Amazon EC2, S3, Athena, Glue, QuickSight, and Lambda, he also leverages Python and SQL scripting to build efficient ETL processes. Vinay has extensive experience in creating automated workflows using AWS services, transforming and organizing data, and developing insightful visualizations with Amazon QuickSight. His work ensures that data is collected efficiently, structured effectively, and made analytics-ready to drive informed decision-making.


 Login
Login


 July 29, 2025
July 29, 2025 PREV
PREV











Comments