|
Voiced by Amazon Polly |
Introduction
This blog will help you set Azure Active Directory level authentication to access Point-to-Site VPN from the user’s machine. It adds a level of security to your Azure infrastructure. The tunnel type should be Open VPN(SSL) to create the AAD authentication. This solution is helpful for end-users who want to connect to Azure VNets centers from a remote location, such as from home or a conference. You can also keep track of all the connections made to Azure VNet using P2S VPN with the help Azure Virtual Network gateway.
Start Learning In-Demand Tech Skills with Expert-Led Training
- Industry-Authorized Curriculum
- Expert-led Training
Prerequisites
- Virtual Network (VNet)
- VM inside above VNet
- Azure AD Tenant
Configuring Virtual Network gateway
- Login to Azure Portal
- Go to Virtual Network Gateway service from Azure portal and click on create to fill the data
- mayank-MPN is the subscription, VGW-Dev as gateway name, now select the region of your Virtual Network, after that Virtual Network will automatically appear into the Virtual Network Section, SKU as VpnGw1 (includes max 250 connections with 640 Mbps throughput) and keep other options as the default shown in below screenshot.

- Provide the gateway subnet range, or else it will automatically create based on CIDR, also created Public Ip named VGW-PIP-dev and keep other option as default mentioned in the below screenshot.

- Provide appropriate tags for the resources. Now click on click + Create and then click on Review + create.
Configuring AAD Authentication
- Log in to the Azure portal as a user assigned the Global administrator access.
- Go To Azure Active Directory Service. Under Properties, the page got to Tenant ID and copy it as shown in the below screenshot.

- Next, Copy and paste the below URL in the browser the below URL is for Azure Public and add the Azure VPN application to your AAD https://login.microsoftonline.com/common/oauth2/authorize?client_id=41b23e61-6c1e-4545-b367-cd054e0ed4b4&response_type=code&redirect_uri=https://portal.azure.com&nonce=1234&prompt=admin_consent
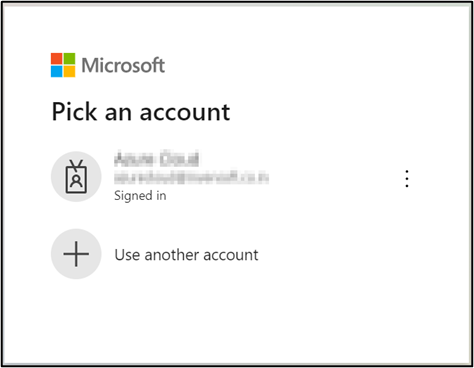

- Select the Global Admin account if prompted and accept the permission request.
- Now in AAD under Enterprise application, Azure VPN application will be added
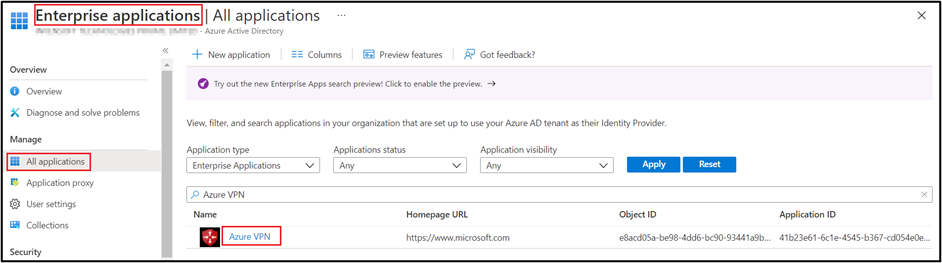
- To add Azure AD authentication on the VPN gateway. First, go to Virtual Network gateway Service -> Point-to-Site configuration and select OpenVPN (SSL) as the Tunnel type. Next, select Azure Active Directory as the Authentication type, then provide the below information under the Azure Active Directory section.
- Tenant: https://login.microsoftonline.com/{AzureAD TenantID}/
- Audience ID (For Azure Public): 41b23e61-6c1e-4545-b367-cd054e0ed4b4
- Issuer (For Secure token Service): https://sts.windows.net/{AzureAD TenantID}/
- Click on Save and then click on Download VPN client to download file.

- Extract the downloaded zip file and browse to the unzipped “AzureVPN” folder.
- Location of the “azurevpnconfig.xml” file from the extracted folder. The azurevpnconfig.xml contains the setting for the VPN connection and can be imported directly into the Azure VPN Client application. The user will need valid Azure AD credentials from your tenant to connect successfully.
Checking the VPN Connection
- Now Open Microsoft store and download Azure VPN Client, and open it once downloaded
- Open the Azure VPN Client and click on Import as shown in the below screenshot

- Now Select the azurevpnconfig file which we received while extracting the folder in the above steps. After that, click on save

- Now click on connect to connect with VPN using Azure AD credentials
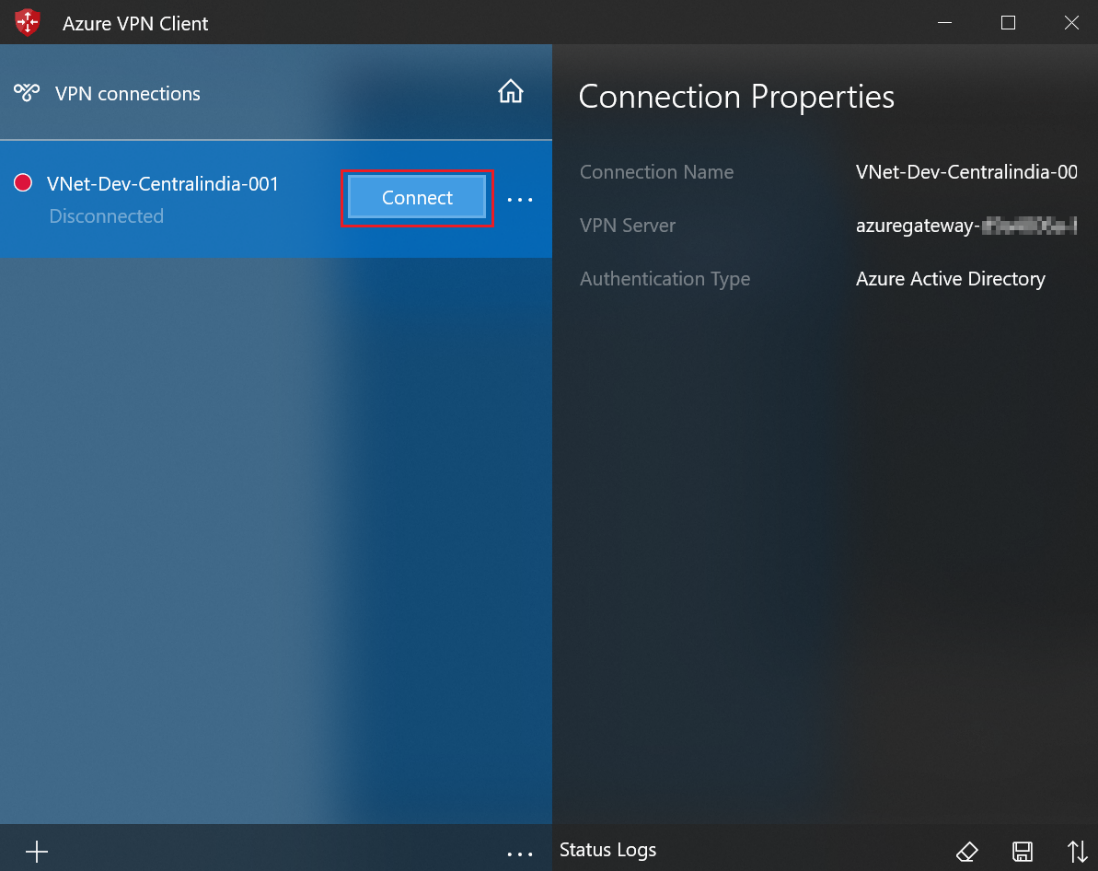
- After that select your Azure AD account and click on Continue

- Once it gets connected successfully the icon will turn green and display connected

- You can now check that your machine will receive IP from the Point-to-Site Address poll

- Now you can RDP into the Azure VM using VMs Private IP for me it is 10.2.1.4

Conclusion
A VPN connection establishes a secure connection between you and the internet. A P2S connection is established by starting it from the client’s computer. With the help of Azure Active Directory (AAD) security benefits, you can centrally create and manage users across your hybrid enterprise, keeping users, groups, and devices synchronized. Provide SSO access to your end applications with an additional layer of security and easy management.
Upskill Your Teams with Enterprise-Ready Tech Training Programs
- Team-wide Customizable Programs
- Measurable Business Outcomes
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.

WRITTEN BY Mayank Bharawa


 Login
Login


 March 11, 2022
March 11, 2022 PREV
PREV











Rishi Raj
Mar 14, 2022
Great source of knowledge
Shreya
Mar 13, 2022
Good work
Akhilesh
Mar 13, 2022
Good work