|
Voiced by Amazon Polly |
As organizations rapidly adopt SaaS platforms, one risk consistently rises to the surface- OAuth app misuse. Attackers increasingly target cloud apps to bypass authentication controls, access sensitive data and establish long-term persistence within enterprise environments. This is where Microsoft Defender for Cloud Apps (MDCA) steps in with its powerful OAuth App Governance capabilities.
In this blog, we explore how App Governance enhances your security posture, why it matters in modern, identity-driven ecosystems and how organizations can operationalize it as part of their Security Operations strategy.
Freedom Month Sale — Upgrade Your Skills, Save Big!
- Up to 80% OFF AWS Courses
- Up to 30% OFF Microsoft Certs
- Ends August 31
Understanding the Need for OAuth App Governance
Modern enterprises rely on thousands of cloud applications, many of which require elevated permissions to access Microsoft 365 data. While this improves productivity, it also introduces significant risks:
- Malicious or over-permissioned applications gaining access to user mailboxes
- Consent phishing bypassing traditional authentication controls
- Impossible-to-detect persistence techniques using long-lived refresh tokens
OAuth App Governance in MDCA provides in-depth visibility into these applications, helping security teams detect anomalies before they escalate.
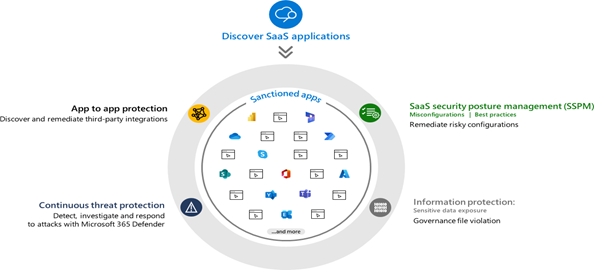
Source Link: Microsoft Defender for Cloud Apps
Key Capabilities of Microsoft Defender for Cloud Apps OAuth App Governance
App Governance enhances protection with intelligent analytics and anomaly detection. It monitors the behavior of apps leveraging Microsoft Graph and flags suspicious patterns such as:
- Unusual data access volume
- Sudden privilege escalations
- High-risk permissions (e.g., reading mail, accessing user profiles)
- Interactions with sensitive data sources
App Governance empowers security teams with actionable insights across app activity, publisher reputation, permission levels and operational risks. It helps enforce stringent application controls without compromising user productivity.
How App Governance Supports Identity and Cloud Security
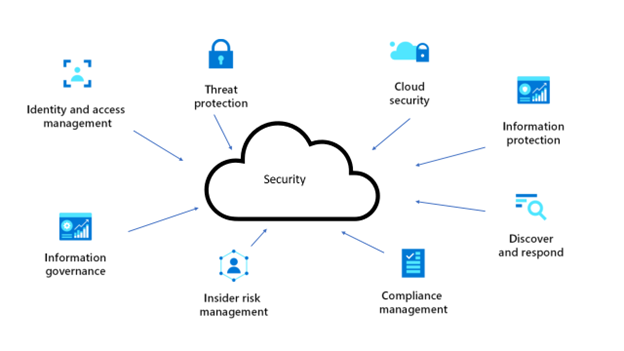
Source link: Security Architecture Design
App Governance is an essential component of a Zero Trust model, addressing identity-driven threats. It enhances cloud security in several ways:
- Deep Visibility Across All OAuth Apps
Security teams can monitor every app used within the tenant, including sanctioned, unsanctioned and shadow IT apps.
- Behavioral Analytics for Advanced Threat Detection
Machine learning identifies deviations in app usage patterns, for example, excessive API calls or sudden access to high-value resources.
- Governance Controls for Continuous Protection
Organizations can define governance rules to control permission levels, enforce publisher verification and restrict high-risk application actions.
- Integration with SOC Workflows
Alerts and insights flow seamlessly into SIEM and XDR platforms, enabling analysts to correlate user, device and application behavior for faster incident response.
Real-World Scenarios Where App Governance Prevents Breaches
- Consent Phishing Attack
An attacker tricks an employee into granting access to a malicious app. App Governance detects abnormal token activity as the app attempts to export email data.
- Compromised OAuth Token
An app begins performing rapid, automated API calls inconsistent with its normal behavior. Governance alerts SOC teams before data can be exfiltrated.
- Over-permissioned Third-Party Apps
A legitimate app requests broad permissions such as Read. All or Mail.ReadWrite. Governance flags the unnecessary privilege and assists administrators with remediation.
These capabilities strengthen your identity perimeter and reduce the risk of cloud-native attacks.
Why App Governance is Essential for Modern Security Operations
App Governance reinforces the foundation of secure identity management by ensuring:
- Least privilege is strictly enforced
- All cloud apps are continuously monitored
- Risky behaviour is quickly detected and mitigated
- SOC teams gain complete control over app-based access
By integrating App Governance into your Security Operations strategy, you establish stronger identity protection, reduce attack surfaces and ensure compliance with organisational security policies.
Securing OAuth App Access
OAuth app abuse continues to be a top vector for cloud-based attacks. With Microsoft Defender for Cloud Apps and its advanced OAuth app governance capabilities, organizations can effectively monitor, control and secure third-party and enterprise apps that interact with sensitive cloud data.
Incorporating these tools into your broader cloud security and Security Operations framework ensures that your environment remains resilient against evolving identity threats.
Freedom Month Sale — Discounts That Set You Free!
- Up to 80% OFF AWS Courses
- Up to 30% OFF Microsoft Certs
- Ends August 31
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.

WRITTEN BY Navitha Wilson
Navitha Wilson is a Microsoft Certified Trainer and Subject Matter Expert in Azure Infrastructure and Architecture at CloudThat, with a strong focus on Microsoft Azure and Hybrid Infrastructure. With over 13 years of experience in training and academics, she has empowered 5,000+ professionals and learners through her expertise in Azure Administration, Networking and Security. She is also a Cisco Certified Network Professional (CCNP) in Routing and Switching, with robust hands-on experience across cloud and on-premises environments. Renowned for her ability to simplify complex technical concepts and deliver engaging hands-on sessions, Navitha consistently receives outstanding feedback from learners and is widely recognized as an exceptional trainer. Her training style blends deep technical knowledge with practical application, ensuring impactful and results-driven learning experiences. Navitha’s passion for technology and reading fuels her unique and inspiring approach to learning and development.


 Login
Login


 December 18, 2025
December 18, 2025 PREV
PREV











Comments