|
Voiced by Amazon Polly |
Introduction
As modern applications evolve, the demand for secure, flexible, and centralized identity management becomes more critical. While AWS IAM is the default choice for controlling access to AWS resources, it does not provide full-fledged capabilities for user authentication, SSO, OAuth/OIDC, or identity federation required by application teams.
This is where Keycloak, a powerful open-source identity provider, steps in.
This blog explains why Keycloak is widely used, even within AWS environments, how it compares with AWS IAM, provides real-world use cases, and highlights the key components that make Keycloak a comprehensive authentication solution.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
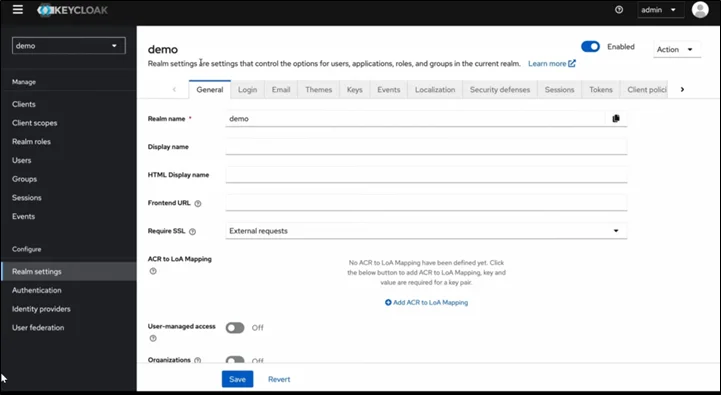
Keycloak Components (Core Building Blocks)
Keycloak provides a rich, modular identity platform. Below are the main components that form its architecture:
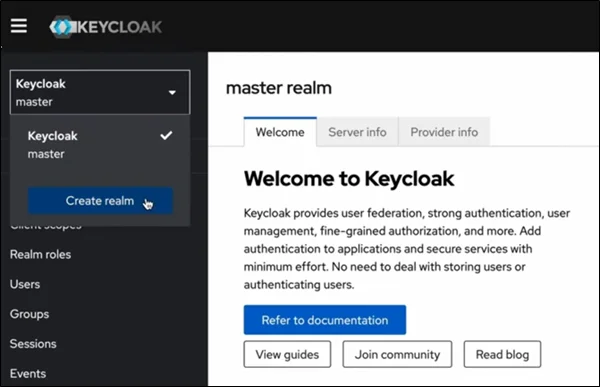
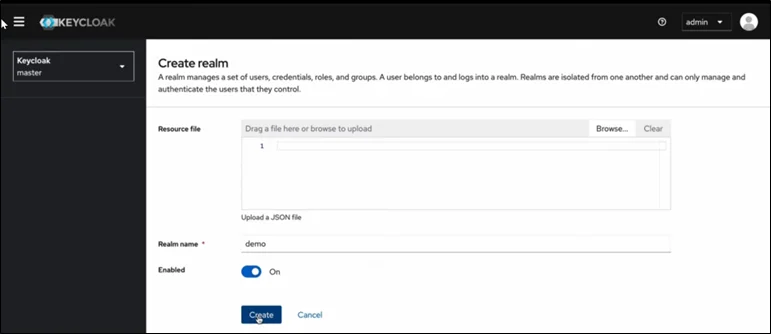
- Realms
A realm is an isolated security domain.
- Each realm has its own users, clients, roles, authentication flows, and configurations.
- Perfect for multi-tenant SaaS applications.
- Users
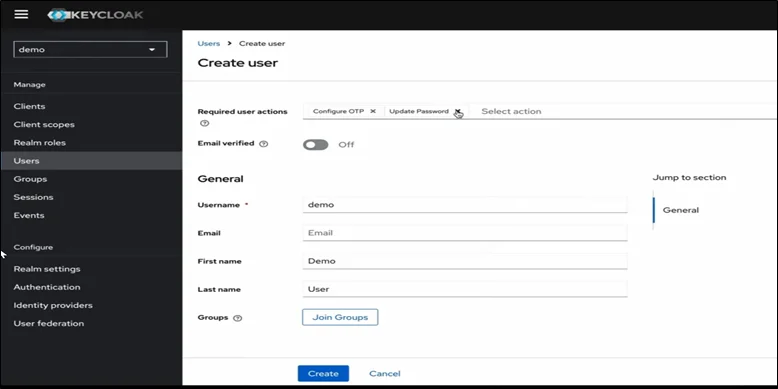
End users who authenticate into applications.
- Keycloak stores user credentials, attributes, groups, and permissions.
- Supports external user federation (LDAP, AD).
- Clients
Applications that use Keycloak for authentication.
- Can be web apps, mobile apps, APIs, or services.
- Integrated using OIDC, OAuth2, or SAML.
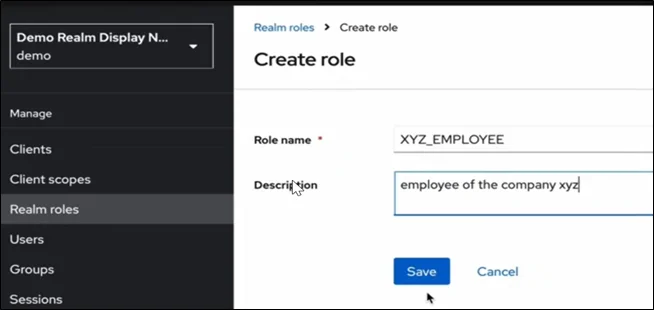
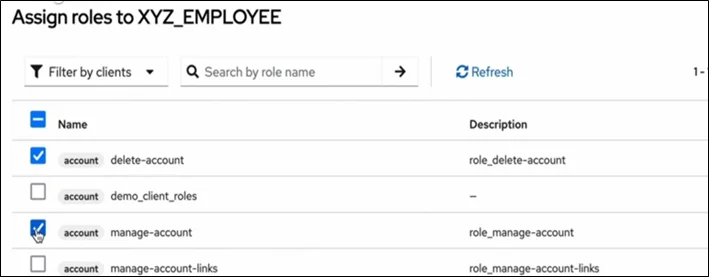
- Roles & Groups
Used for authorization within applications.
- Realm roles: Global roles at realm level.
- Client roles: Roles specific to an application.
- Groups: Organize users and apply role mappings efficiently.
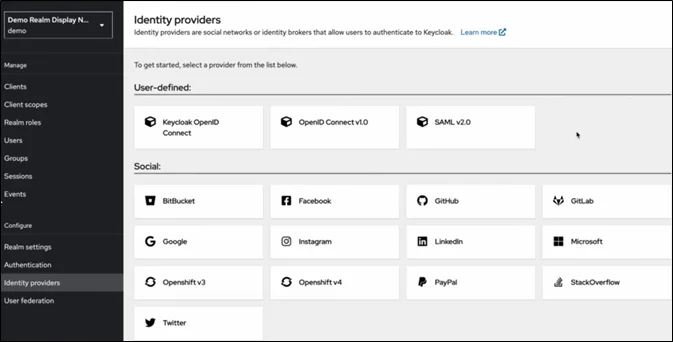
- Identity Providers (IdPs)
Allows external authentication via:
- Azure AD / Okta
- Google Workspace
- LDAP / Active Directory
- Social logins
Keycloak becomes a broker between applications and external IdPs.
- Authentication Flows
Defines the user login experience.
Includes:
- Username/password
- Multi-factor authentication
- Conditional workflows
- Custom authenticators using SPI
Extremely flexible for enterprise-grade security.
- Protocol Mappers
Transform or add custom claims inside JWT/OIDC tokens.
Useful when your application needs additional user attributes (email, roles, tenant info).
- Admin Console
UI for managing realms, clients, roles, policies, and users.
- Account Console
A self-service interface allowing users to:
- Update profile
- Reset password
- Manage sessions
- Manage MFA
- Keycloak Storage (Database Layer)
Stores configuration, tokens, and user data.
Often backed by:
- PostgreSQL (most common)
- Amazon RDS / Aurora in AWS deployments
How Keycloak Is Useful Compared to AWS IAM?
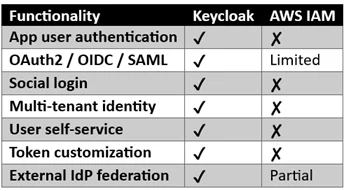
In short:
- AWS IAM → Controls access to AWS services
- Keycloak → Handles authentication & SSO for your applications
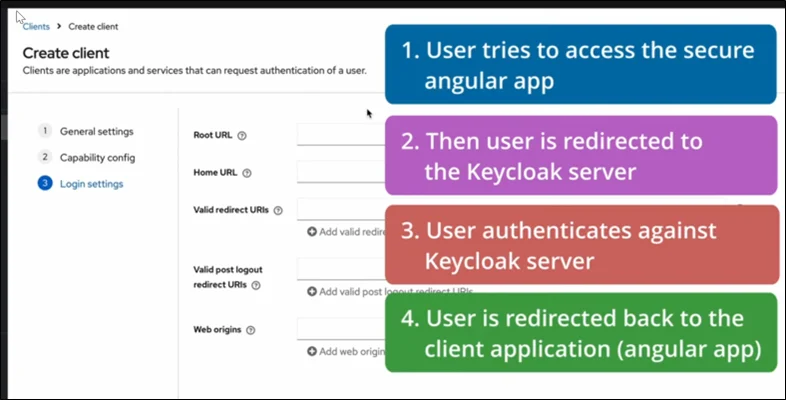
Specific Use Case: SaaS Application Deployed on Amazon EKS
A multi-tenant SaaS application requires isolated identity domains.
Keycloak Advantages:
- Create one realm per tenant.
- Each realm gets custom branding, MFA, and user sets.
- Integrate each tenant’s corporate IdP (Azure AD / Okta) easily.
- Applications on Amazon EKS validate JWTs from Keycloak.
Why AWS IAM Cannot Be Used:
- AWS IAM users are not meant for application login.
- No support for multi-tenant realms or user self-service.
- No custom SSO flows.
Keycloak becomes the ideal identity hub in AWS.
Conclusion
AWS IAM and Keycloak are complementary, not competing, solutions.
AWS IAM secures AWS infrastructure, while Keycloak secures end-user access to applications.
For modern cloud-native applications, especially SaaS products, Keycloak running on AWS (Amazon EKS, Amazon ECS, or Amazon EC2) delivers unmatched flexibility, federation capabilities, and user management features.
Drop a query if you have any questions regarding AWS IAM or Keycloak and we will get back to you quickly.
Making IT Networks Enterprise-ready – Cloud Management Services
- Accelerated cloud migration
- End-to-end view of the cloud environment
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. Is Keycloak better than AWS IAM Identity Center?
ANS: – Use AWS IAM Identity Center if your goal is to provide SSO access to AWS Console and enterprise SaaS apps.
Use Keycloak for custom apps, multi-tenancy, and advanced authentication workflows.
2. Can Keycloak integrate with AWS services?
ANS: – Yes. Applications running on AWS (Amazon EKS, AWS Lambda, Amazon EC2, Amazon API Gateway) can validate Keycloak-issued JWT tokens.
3. Is Keycloak free?
ANS: – Yes, Keycloak is open-source and free to use. You only pay for AWS infrastructure where it is hosted.

WRITTEN BY Deepika N
Deepika N works as a Senior Research Associate - DevOps and holds a Master’s degree in Computer Applications. She is passionate about DevOps and related technologies. Deepika has strong expertise in AWS and Azure DevOps, Kubernetes (EKS), Terraform, and CI/CD pipelines. She is proficient in infrastructure as code, automation, monitoring, security enforcement, and multi-cloud deployment strategies. Skilled in version control, infrastructure documentation, cloud-native technologies, and managing production workloads, container platforms, and DevSecOps practices, Deepika brings comprehensive hands-on experience to her role.


 Login
Login


 December 22, 2025
December 22, 2025 PREV
PREV











Comments