|
Voiced by Amazon Polly |
In the modern data landscape, credentials and secrets are a major liability when managing data platforms. Hard-coding them into pipelines and connections introduces risk. Thankfully, the integration of Azure Key Vault (AKV) with Microsoft Fabric’s data-factory layer offers a secure alternative: you don’t store the secret in Fabric, you reference it. In this blog, we’ll walk you through why you should use AKV references in Fabric, how they work at a high level and then step-by-step instructions on how to configure them.
Start Learning In-Demand Tech Skills with Expert-Led Training
- Industry-Authorized Curriculum
- Expert-led Training
Why Use Azure Key Vault References in Microsoft Fabric
Here are the benefits and considerations:
- No hard-coded secrets: With AKV references, Fabric only stores the vault URI and secret name (and authentication details) – the actual secret value stays in Azure Key Vault.
- Dynamic retrieval at runtime: When a data connection needs the credential, Fabric fetches the secret from Key Vault, uses it in-memory only and doesn’t persist it.
- Consistent with least-privilege / secrets hygiene: Centralizing secrets in AKV means you can rotate them, audit access and apply governance rather than embedding them in many disparate connections.
- Supported across many connectors: Fabric supports AKV-references for various connector types (Blobs, ADLS Gen2, Databricks, OData, Snowflake, etc).
Limitations to be aware of:
- Azure Key Vault references are currently available for cloud connections only.
-
- Virtual-network data gateway connections aren’t supported with this feature yet.
- Fabric always retrieves the latest version of a secret; version-specific retrieval (of older secret versions) is not supported.
For more details, you can visit the Microsoft Official Documentation website.
How Azure Key Vault References Works
Fig. 1: Conceptual Flow
Microsoft Fabric uses Azure Key Vault references to securely manage secrets without storing them in pipelines, notebooks or connections. A Key Vault reference establishes a trusted connection between Fabric and an Azure Key Vault, utilizing Microsoft Entra ID (OAuth 2.0).
Once this trust is established, the reference becomes a reusable workspace-level asset. When creating a supported connection, instead of entering a password or key, you bind the required credential field to a Key Vault secret. Fabric stores only the reference and secret name, not the secret value.
At runtime, Fabric securely fetches the secret from Azure Key Vault, injects it into memory and uses it to access the data source. Secrets are never exposed, logged or persisted in Fabric items.
This approach enables centralized secret management, secure credential rotation, improved governance and environment consistency across Fabric workloads.
Supported Connectors and Authentication Types
Microsoft Fabric supports Azure Key Vault references across a wide range of connectors, each offering different authentication methods to access data sources securely. Depending on the connector, users can authenticate using account keys, basic username/password, SAS or personal access tokens, or service principals. The table highlights which authentication types are supported for each connector, making it easier to choose the right method when configuring secure, AKV-enabled connections in Fabric.
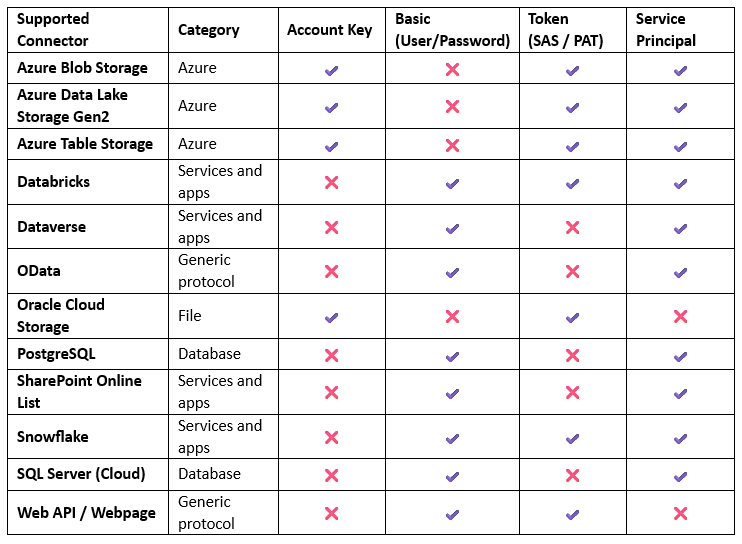
Table 1: Source Microsoft Fabric
Secure Fabric Credentials
Azure Key Vault References provide a secure and efficient way to manage credentials in Microsoft Fabric by retrieving secrets directly from Key Vault at runtime, thereby eliminating the need to store sensitive values in Fabric connections. With the new preview capabilities, organizations can strengthen their security posture, simplify secret rotation and maintain centralized governance across data engineering workloads. Adopting Key Vault-based authentication is a best practice for teams building reliable and compliant data solutions in Microsoft Fabric.
Upskill Your Teams with Enterprise-Ready Tech Training Programs
- Team-wide Customizable Programs
- Measurable Business Outcomes
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.

WRITTEN BY Pankaj Choudhary
Pankaj Choudhary is the Azure Data Vertical Head at CloudThat, specializing in Azure Data solutions. With 14 years of experience in data engineering, he has helped over 5,000 professionals upskill in technologies such as Azure, Databricks, Microsoft Fabric, and Big Data. Known for his ability to simplify complex concepts and deliver hands-on, practical learning, Pankaj brings deep technical expertise and industry insights into every training and solution engagement. He holds multiple certifications, including Databricks Certified Data Engineer Associate, Microsoft Certified: Azure Data Engineer Associate, and Apache Spark Developer. His work spans building scalable Lakehouse architectures, designing PySpark-based ETL pipelines, enabling real-time analytics, and implementing CI/CD pipelines with Azure DevOps. Pankaj’s passion for empowering teams and staying at the forefront of data innovation shapes his unique, outcome-driven approach to learning and development.


 Login
Login


 December 22, 2025
December 22, 2025 PREV
PREV











Comments