|
Voiced by Amazon Polly |
In today’s rapidly evolving digital landscape, cybersecurity is no longer a “nice-to-have”, it’s a business imperative. Organizations face an increasing number of threats, from phishing attacks to sophisticated ransomware campaigns. As enterprises move toward hybrid work and cloud-first operations, traditional perimeter-based security models fall short. This is where Microsoft 365 Security Training steps in- not just as a learning path, but as a roadmap to a Zero Trust ecosystem.
Freedom Month Sale — Upgrade Your Skills, Save Big!
- Up to 80% OFF AWS Courses
- Up to 30% OFF Microsoft Certs
- Ends August 31
Understanding Zero Trust: The New Security Mindset
The concept of Zero Trust is simple yet revolutionary: Never trust, always verify. Instead of assuming everything inside the corporate network is safe, Zero Trust treats every access request as a potential threat.
Microsoft’s Zero Trust framework revolves around three key principles:
- Verify explicitly – Always authenticate and authorize based on all available data points.
- Use least-privilege access – Limit user access to only what’s necessary for their role.
- Assume breach – Design security systems under the assumption that attackers are already inside.
With Microsoft 365, these principles are not theoretical; they’re built into the tools businesses use every day.
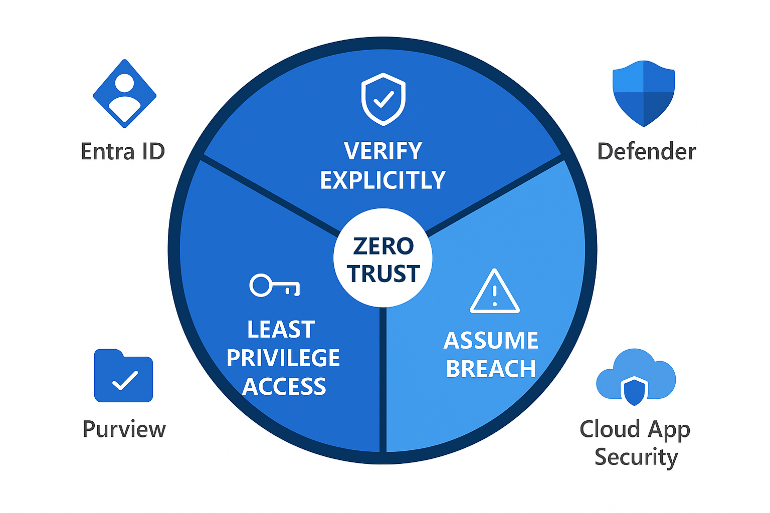
Source: Microsoft Learn
Microsoft 365 Security: Beyond the Basics
Microsoft 365 offers a unified suite that brings together identity, endpoint and data protection under one roof.
Here’s how the platform reinforces Zero Trust through its security layers:
- Identity and Access Management (IAM) – Services like Microsoft Entra ID (formerly Azure AD) ensure secure user identities, multi-factor authentication (MFA) and conditional access policies.
- Device and Endpoint Protection – Microsoft Defender for Endpoint continuously monitors devices, detects threats and isolates compromised assets.
- Information Protection and Compliance – Microsoft Purview (formerly Compliance Center) classifies and protects data across environments.
- Cloud App Security – Defender for Cloud Apps provides visibility into shadow IT and helps enforce app governance.
Training employees to use these tools effectively turns your Microsoft 365 environment into a living, adaptive security ecosystem.
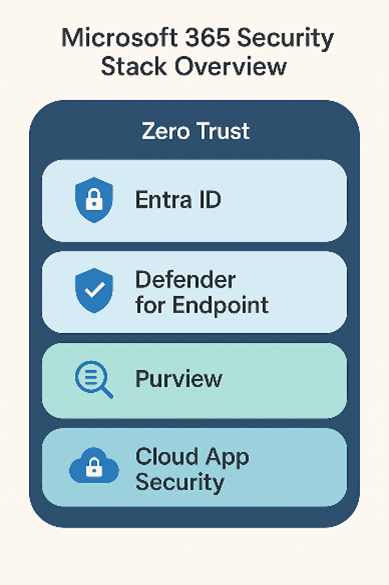
Fig 2: Microsoft 365 Security Stack Overview
Why Microsoft 365 Security Training Matters
Technology alone cannot achieve Zero Trust. People are the strongest, and sometimes the weakest, link in the chain. Security training empowers employees, IT admins and decision-makers to align technology with human vigilance.
Fig 3: Learning Path or Training Flow
Building a Culture of Continuous Vigilance
Zero Trust isn’t a one-time setup: it’s an evolving culture. Regular security awareness sessions, simulation-based learning and policy audits help organizations stay ahead of threats.
A well-trained workforce ensures that identity verification, device protection and data governance are not just IT checkboxes but daily habits.
When employees understand the why behind every security policy, compliance transforms from obligation to ownership.
Fig 4: Security Culture in Action
The Future is Trustless and That’s a Good Thing
Enterprises that invest in Microsoft 365 Security Training don’t just adopt new tools- they adopt a new mindset. The Zero Trust model ensures that every identity, device and data interaction is protected. It transforms security from a reactive stance to a proactive shield.
Ultimately, hardening the enterprise is not about building taller walls; it’s about building smarter, more adaptive defences. And that begins with the right training.
Freedom Month Sale — Discounts That Set You Free!
- Up to 80% OFF AWS Courses
- Up to 30% OFF Microsoft Certs
- Ends August 31
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.

WRITTEN BY Reshu Goyal
Reshu Goyal is a Microsoft Certified Trainer and Subject Matter Expert at CloudThat with over 10 years of experience in data analytics and visualization. She has trained 1,000+ professionals across Power BI, Microsoft Fabric, Advanced Excel and Tableau, delivering sessions for top clients like Microsoft, Deloitte and TCS. Reshu is known for her hands-on, learner-focused approach and her ability to turn complex data into actionable insights.


 Login
Login


 December 15, 2025
December 15, 2025 PREV
PREV











Comments