|
Voiced by Amazon Polly |
Overview
The blog is about container runtime. The container runtimes which are currently available mostly compliant with the Open Container Initiative (OCI) Runtime Specification. This blog provides an introduction to runC.
runC is a container runtime based on the Runtime Specification of the Linux Foundation (runtime-spec). The Open Container Initiative created runC. Oracle Linux Cloud Native Environment includes runC. runC is a Cloud Native Computing Foundation (CNCF)-compliant environment for microservices and container orchestration. runC is based on the upstream runC project’s stable release. Oracle-specific fixes and patches for specific bugs are the only differences between Oracle versions of the software and upstream releases.
Start Learning In-Demand Tech Skills with Expert-Led Training
- Industry-Authorized Curriculum
- Expert-led Training
Introduction
A software element that may execute containers on a host operating system is referred to as a container runtime or container engine. Container runtimes in a containerized architecture are in charge of loading container images from a repository, keeping track of local system resources, isolating system resources for usage in a container, and controlling the lifecycle of containers.
Container Runtime Types
Container runtimes come in three basic categories.
- Low-level runtimes
- High-level runtimes
- Sandboxed or virtualized runtimes.
Low-Level Container Runtimes
To provide open standards for Linux containers, Docker initiated the Open Container Interface (OCI) Linux Foundation initiative.
A low-level container runtime called runC carries out the OCI standard.
runC was developed by the OCI and Docker. Today, it serves as the low-level container runtime as per de facto standard. runC is implemented using Go. It is constantly being monitored and updated by moby as part of Docker’s open source project, moby.
OCI (Open Container Initiative)
The OCI is a mechanism for open governance that makes decisions about container runtimes and formats (created by Docker, CoreOS, etc.).
To make things uniform, it simply establishes criteria and standards that apply to containers.
There are mainly two specifications:
- Runtime definition to specify how a container functions and its lifecycle while running.
- For example, when you run docker container create golang:alpine, it describes how exactly your docker container works.
- According to the standard, an OCI-spec container must have certain attributes.

2. A container image’s standard format is defined by an image specification.
Both containerd and cri-o use runC to list OCI specifications.
- OCI specifies how a container should be set up, run, and executed, as well as what should be included in its state, among other things.
- runC is a lightweight and universal container runtime that manages all of the low-level intricacies of launching a container as well as Linux primitives such as cgroups and namespaces that handle a container’s system and resource isolation.
- cri-o or containerd control the lifetime of a container, from image execution through supervision, networking, and container death.
- Extra – Docker (or, more properly, dockerd) is a containerd* abstraction. It also handles orchestration, scalability, and volume, among other things.
runC is a small, portable container runtime. It contains all of the plumbing code needed by Docker to communicate with container-related system features. It is built around the following principles:
- Designed for safety.
- Usable at large scale, in production, today.
- There is no dependence on the rest of the Docker platform: only the container runtime is required.
The following are popular runC features:
Full Linux namespace support, including user namespaces
- All security technologies available in Linux are supported natively, including Selinux, Apparmor, seccomp, control groups, capability drop, pivot root, uid/gid dropping, and so on. If Linux can do it, so can runC.
- Parallels’ CRIU team assisted in providing native support for live migration.
- Microsoft engineers are actively contributing native support for Windows 10 containers.
- Native Arm, Power, and Sparc support are planned, with direct engagement and support from Arm, Intel, Qualcomm, IBM, and the full hardware maker ecosystem.
- Native support for cutting-edge hardware features like DPDK, sr-iov, tpm, secure enclave, and so on is planned.
- Google engineers supplied portable performance characteristics based on their experience deploying containers in production.
- The Open Container Project, under the auspices of the Linux Foundation, governs an officially described configuration format. In other words, it’s a true benchmark.
Steps to Set up VM
Step 1 – Login into AWS Account and search for EC2 instances. Choose Launch Instances

Step 2 – Select the OS here that ubuntu has chosen.

Step 3 – Select the instance type and key pair

Step 4 – Select the Security Group and the default rules as shown below and click on Launch instances
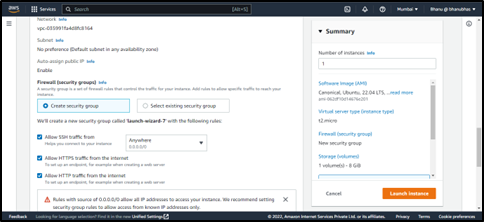
Step 5 – After the successful creation of the Instance you will get the landing page and copy the public Ip from there

Step 6 – Connect to the instance and follow the procedure mentioned below


RunC’s goal is to make standard containers available everywhere.
Step 7 – To install runC on the system use the apt install runc command
|
1 2 |
apt update apt install runc -y |

Figure 1: Installation of runc
Check whether runC is installed or not on the system use the runc command
|
1 |
runc the container runtime- runc |

Figure 2: Checking Runc
Usually, we need an image for running the container with runC. Deboostrap is an image used to install a Debian-based system into a subdirectory of another, already installed system through the command sudo apt install debootstrap –y.

Figure 3: Installing deboostrap
Step 8 – After that create a new directory in /mnt/chroot-ubuntu-trusty
|
1 2 |
sudo mkdir /mnt/ sudo mkdir /mnt/chroot-ubuntu-trusty |
![]()
![]()
Step 9 – Then use debootstrap, to install a Ubuntu distribution in the directory created earlier with the command specified below.
|
1 |
cd /mnt/chroot-ubuntu-trusty |

|
1 |
sudo debootstrap trusty /mnt/chroot-ubuntu-trusty http://archive.ubuntu.com/ubuntu/ |

Navigate to /mnt/ directory created earlier.
|
1 |
cd /mnt/ |
![]()
After getting the image, make a sample spec such that to run the containers using the runc spec command
|
1 |
runc spec |
![]()
After running this, we will get a config.json file in the current directory along with the chroot-ubuntu-trusty directory, which helps to create the container which can be seen through the ls command.
ls
![]()
This config.json file has the information about configurations to run the containers like oci version, os architecture, etc.
Step 10 – Change the config.json file by using the following nano/vim editor, which is located in the ‘root’ section ‘path’ that consists of the value of ‘rootfs’ that indicates the current image location, the image location is ‘chroot-ubuntu-trusty’.
Generating OCI Configuration
Change the ‘rootfs’ with ‘chroot-ubuntu-trusty’
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
{ "ociVersion": "1.0.2-dev", "process": { "terminal": true, "user": { "uid": 0, "gid": 0 }, "args": [ "sh" ], }, ....... "root": { "path": "rootfs", # replace "rootfs" with "chroot-ubuntu-trusty” "readonly": true }, "hostname": "runc", "mounts": [ ......... |
Then run a container with the runc command
runc run myc
The myc is nothing but the name of the container. runC usually finds the config.json file and it usually creates the container with myc name that runs a shell program in it and opens a shell. Exit command is used to exit from the shell.

Figure 4: Shell in myc container
In the config.json file, there we can change the ‘args’ to ‘date’ it is currently ‘sh’ which is used to get the current date when the container is up and runs.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 |
{ "ociVersion": "1.0.2-dev", "process": { "terminal": true, "user": { "uid": 0, "gid": 0 }, "args": [ "sh" # replace "sh" with "date" ], }, ....... "root": { "path": "rootfs", # replace "rootfs" with "chroot-ubuntu-trusty" "readonly": true }, "hostname": "runc", "mounts": [ ......... |
Hence after all the changes getting saved, later on running the container again, the result usually fetches the current date instead of the shell program.
runc run myc
![]()
Figure 5: Shell in myc container
Conclusion
Runc is a powerful tool that is typically used by higher-level runtimes. This is because runc is a very low-level runtime on its own. It lacks many securities enhancement features out of the box, such as seccomp, SELinux, and AppArmor. Nonetheless, the tool supports the security enhancements natively, but they are not included in the default configurations.
Upskill Your Teams with Enterprise-Ready Tech Training Programs
- Team-wide Customizable Programs
- Measurable Business Outcomes
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. What is the main use of Runtime specifications?
ANS: – This spec aims usually defines configuration, as well as an execution environment, and l finally defines the lifecycle of a container.
2. What is the main use of the Configuration file?
ANS: – The configuration file named config.json provides the whole configuration of the container for the supported platforms and details that the field usually enables the creation of a container. The execution environment is detailed along with the common actions defined for a container’s lifecycle to ensure that applications running inside a container have a consistent environment between runtimes.
3. What is runc?
ANS: – runC is nothing but a CLI tool used mainly for spawning as well as running containers based on the OCI specification.

WRITTEN BY Bhanu Prakash K
K Bhanu Prakash is working as a Subject Matter Expert in CloudThat. He is proficient in Managing and configuring AWS Infrastructure as well as on Kubernetes and DevOps tools like Terraform, ansible, Jenkins, and Git. He is very keen on learning new technologies and publishing blogs for the tech community.


 Login
Login


 December 27, 2022
December 27, 2022 PREV
PREV










Comments