|
Voiced by Amazon Polly |
As enterprises scale to embrace hybrid and multi-cloud architectures, networking and security become top priorities. Microsoft Azure offers a powerful solution — Azure Virtual WAN (VWAN) — designed to simplify and centralize network connectivity across regions, on-premises data centers, and branch offices. But like any global networking platform, securing your Virtual WAN is not optional — it’s essential.
In this blog, we’ll explore what Azure Virtual WAN is, how it works, and most importantly, the security best practices you should adopt to protect your enterprise network.
Start Learning In-Demand Tech Skills with Expert-Led Training
- Industry-Authorized Curriculum
- Expert-led Training
What is Azure Virtual WAN?
Azure Virtual WAN is a networking service that provides a unified hub-and-spoke architecture to connect your branch offices, on-premises data centers, remote users, and Azure Virtual Networks (VNets) across the globe.
It offers:
- Centralized network management
- Built-in security integration
- Scalable connectivity via ExpressRoute, VPN, and SD-WAN
- Simplified routing and policy enforcement
At the heart of VWAN are two key components:
- Virtual WAN Hub: A Microsoft-managed regional resource acting as the central point for connectivity.
- Spokes (VNets, Branches, Users): These connect to the hub, forming a scalable and secure mesh.
Why Use Azure Virtual WAN?
- Global Scale: Connect and manage hundreds of sites and VNets across multiple Azure regions.
- Simplified Networking: Centralized management and automated route propagation.
- Optimized Performance: Intelligent traffic routing and built-in integration with Azure Firewall and security solutions.
- Hybrid and Remote Access: Secure connectivity to users and branches using VPN, SD-WAN, or Azure ExpressRoute.
Key Security Features in Azure VWAN
Azure Virtual WAN isn’t just about connectivity — it bakes security into the architecture. Key features include:
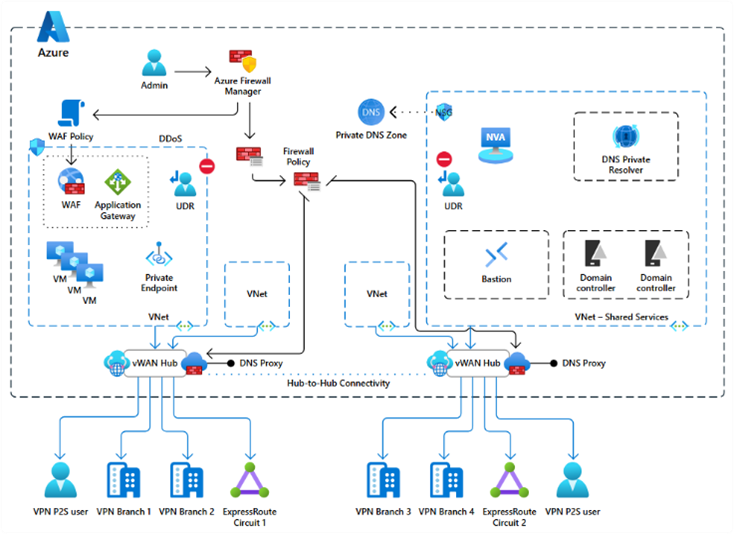
Ref: Apply Zero Trust principles to Azure Virtual WAN | Microsoft Learn
The image illustrates a secure Azure Virtual WAN architecture, showcasing connectivity between branches, VNets, and remote users through a centralized Secured Virtual Hub. Key security components like Azure Firewall Premium, custom route tables, and Azure DDoS Protection are integrated for robust protection.
- Azure Firewall Manager Integration
You can associate Azure Firewall with your VWAN hub, creating a secured virtual hub. This ensures all traffic entering or leaving the network passes through a robust, stateful firewall.
- Hub Virtual Network Security
Use Network Security Groups (NSGs) to control traffic within the hub or between connected VNets.
- Custom Routing Policies
VWAN supports custom route tables, allowing granular control over traffic paths and enforcing traffic inspection rules.
- IPSec Encryption
All VPN tunnels use IPSec/IKE encryption standards, ensuring secure site-to-site and point-to-site traffic.
- Azure Private Link and Service Endpoints
Securely access PaaS services over the Microsoft backbone, reducing exposure to the public internet.
Security Best Practices for Azure Virtual WAN
Let’s walk through a comprehensive set of security best practices when designing, deploying, and managing an Azure VWAN.
- Use Secured Virtual Hubs
Deploy a Secured Virtual Hub that integrates with Azure Firewall or third-party Network Virtual Appliances (NVAs). This allows centralized inspection and control of east-west and north-south traffic.
Best Practice:
- Use Azure Firewall Premium to enable TLS inspection, IDPS (intrusion detection and prevention), and URL filtering.
- Implement Zero Trust Principles
Adopt Zero Trust Networking (ZTN) principles by verifying identity, device posture, and session risk before allowing access to any resource.
Best Practice:
- Integrate Azure Virtual WAN with Azure Active Directory and Microsoft Entra ID Conditional Access to authenticate and authorize remote users.
- Use Azure Private DNS Zones to limit name resolution only to approved domains.
- Enforce Segmentation with Custom Route Tables
By default, traffic between VNets connected to a hub is allowed. Use custom route tables to create segmentation between workloads, environments (dev/prod), or business units.
Best Practice:
- Create separate route tables for different application zones and associate them with specific connections.
- Disable auto-propagation where unnecessary.
- Secure Branch and Remote Connectivity
Use IPSec VPN or ExpressRoute with encryption for secure site-to-site and branch connections.
Best Practice:
- Use Route-based VPN with IKEv2 and strong cryptographic algorithms.
- For ExpressRoute, enable MACsec (Layer 2 encryption) for physical layer protection.
- Integrate with Azure DDoS Protection
Protect against volumetric attacks by enabling Azure DDoS Network Protection on VWAN hubs.
Best Practice:
- Use DDoS Protection Plan with auto-tuning thresholds to adapt to traffic baselines.
- Combine with Firewall logging to detect anomalous behaviour.
- Monitor and Audit Network Traffic
Monitoring is critical for proactive threat detection and compliance.
Best Practice:
- Enable Diagnostics Logs on Virtual WAN resources and export to Log Analytics.
- Use Azure Network Watcher for connection troubleshooting and flow logs.
- Configure Traffic Analytics to visualize traffic patterns.
- Use Secure User VPN Access
Use Azure VPN Gateway in the hub for point-to-site connectivity with multi-factor authentication (MFA).
Best Practice:
- Use OpenVPN or IKEv2 protocols.
- Integrate with Azure AD for identity-based access control.
- Configure split tunneling to restrict internet-bound traffic.
- Secure VNet-to-VNet Communication
Even when connected via VWAN, VNet peering must be controlled to avoid lateral movement in case of compromise.
Best Practice:
- Apply NSGs to VNet subnets to restrict unnecessary traffic.
- Use Azure Firewall to inspect traffic between VNets.
- Automate Security Configuration with Infrastructure as Code
Use ARM templates, Bicep, or Terraform to consistently deploy secure Virtual WAN configurations.
Best Practice:
- Store infrastructure code in version control systems like GitHub or Azure DevOps.
- Apply Azure Policy to enforce secure configurations and prevent drift.
- Regularly Review and Update Security Settings
Security isn’t a one-time setup. Regular reviews ensure compliance and resiliency against evolving threats.
Best Practice:
- Run Microsoft Defender for Cloud assessments.
- Perform penetration testing on exposed services.
- Patch all integrated NVAs and services promptly.
Conclusion
Azure Virtual WAN is a powerful tool that simplifies global network connectivity and security for large-scale enterprises. However, to fully leverage its capabilities, it’s crucial to design and maintain it with a strong security posture.
By applying the security best practices outlined above — from segmentation and firewall integration to DDoS protection and Zero Trust access — organizations can ensure that their cloud networks are not only connected and efficient but also secure and resilient.
Whether you’re beginning your VWAN journey or optimizing an existing deployment, security should remain your top priority.
Reference study courses on above topic:
AZ-700: Designing and Implementing Microsoft Azure Networking Solutions – CloudThat Training
Upskill Your Teams with Enterprise-Ready Tech Training Programs
- Team-wide Customizable Programs
- Measurable Business Outcomes
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.

WRITTEN BY Kunal Khadke
Kunal Khadke is a Subject Matter Expert and Microsoft Certified Trainer at CloudThat, with a strong focus on Microsoft Azure Infrastructure and security. With 10+ years of experience in cloud, he has trained over 5000 professionals. Kunal has a strong passion for empowering IT professionals and organizations on their cloud journey. He has hands-on experience in cloud architecture, deployment, and security. He delivers practical, real-world training that bridges the gap between certification and implementation. Kunal has trained professionals across industries, helping them master Azure services such as Virtual Networks, Azure Active Directory, Security, Networking, and more. Known for his clear teaching style and deep technical knowledge, Kunal is dedicated to shaping the next generation of cloud experts.


 Login
Login


 September 19, 2025
September 19, 2025 PREV
PREV











Comments