|
Voiced by Amazon Polly |
Overview
API security has become paramount in today’s digital landscape as organizations increasingly rely on APIs to power their applications and integrate services. Amazon Cognito User Pools provide a managed identity service that simplifies user authentication and authorization processes, serving as a robust solution for securing API endpoints through JWT token validation.
This approach ensures that only authenticated users with valid tokens can access your API resources, protecting sensitive data and maintaining compliance with security standards.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
Introduction
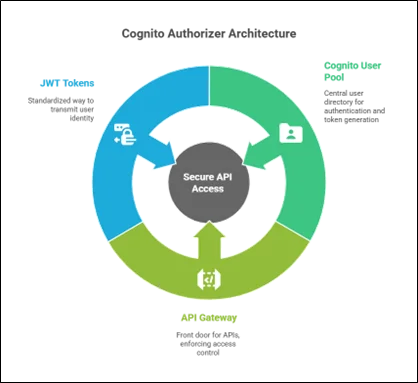
Amazon Cognito authorizers are Amazon API Gateway components that integrate with Amazon Cognito User Pools to validate JWT tokens. When a client requests your API, the authorizer automatically validates the token in the Authorization header, ensuring the user is authenticated before allowing access to the protected resource.
Key Components and Architecture
The Amazon Cognito authorizer architecture involves several key components working together:
- Amazon Cognito User Pool: This central user directory handles user registration, authentication, and JWT token generation. The user pool issues ID tokens (for authentication) and access tokens (for authorization with custom scopes).
- API Gateway Authorizer: A COGNITO_USER_POOLS type authorizer that validates JWT tokens from the Authorization header before allowing access to protected resources.
- JWT Token Validation: The authorizer validates token signatures, expiration times, and token audience claims to ensure authenticity and prevent unauthorized access.
- Backend Integration: Once authenticated, requests are forwarded to your backend services (Lambda functions, HTTP endpoints, or other AWS services).
Implementation Process
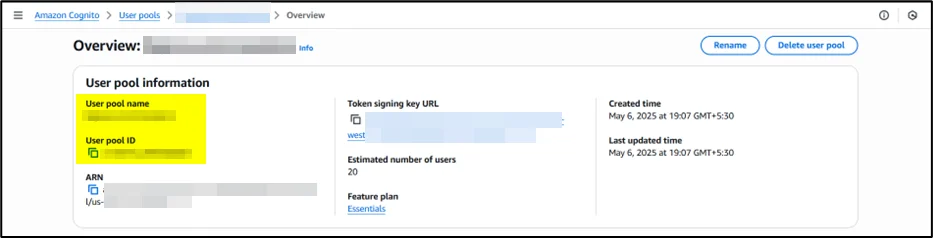
Step 1: Configure Amazon Cognito User Pool
Create a user pool with appropriate sign-in options, password policies, and app client settings. Configure the hosted UI if needed for user registration and authentication workflows.
Step 2: Set Up Amazon API Gateway Authorizer
- Create a REST API in Amazon API Gateway
- Add a resource with the POST method (Authorization = None by default)
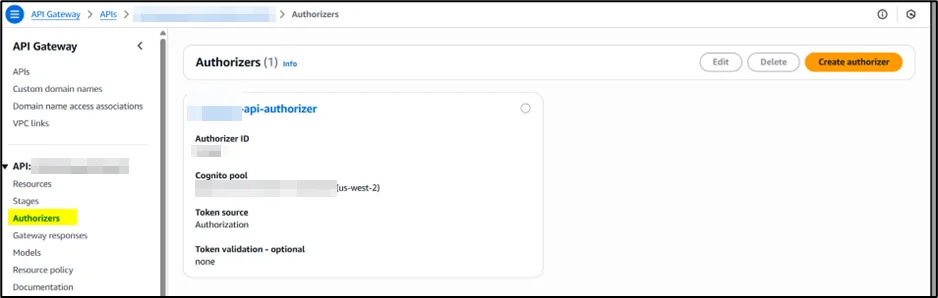
- Navigate to Authorizers → Create Authorizer
- Select Amazon Cognito type and specify your user pool
- Set the token source to the Authorization header
Step 3: Attach Authorizer to API Methods
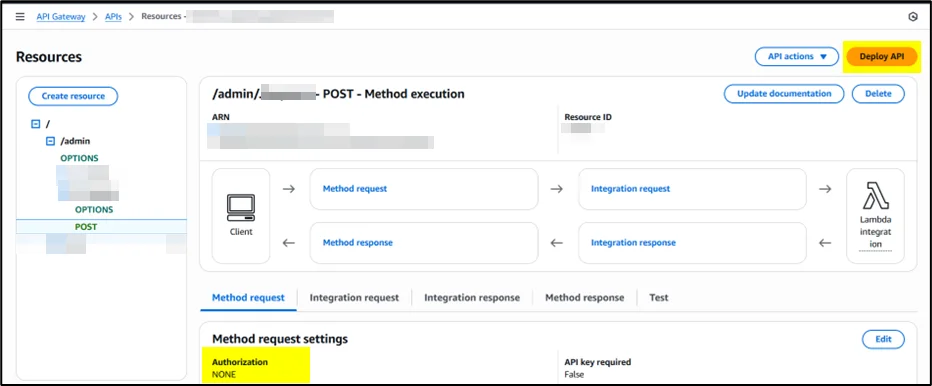
Apply the Amazon Cognito authorizer to specific API methods or resources that require authentication. This ensures that only requests with valid tokens can access protected endpoints.
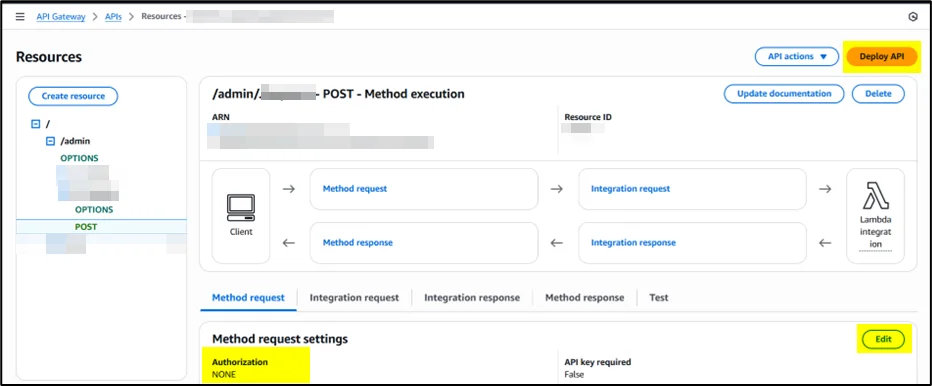
- Edit the POST method’s Method Request settings
- Attach the created authorizer
- Deploy the API to apply security changes
Step 4: Token Management & Run API
Implement proper token handling in client applications, including token refresh mechanisms for long-running sessions and secure token storage practices.
- Pass ID token as Bearer Token in the Authorization header
- Amazon Cognito provides ID token, Access token, and Refresh token (stored in the browser’s local storage)
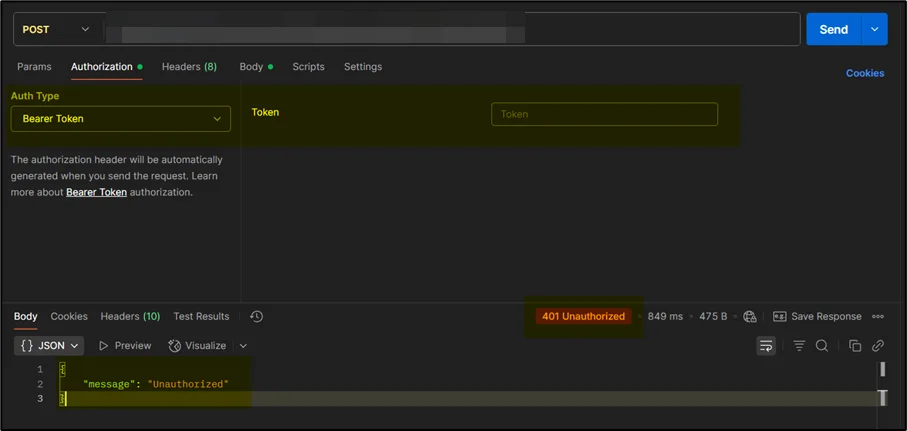
Without Bearer Token: When you test the API without proper authorization, it returns a 401 Unauthorized error with the message “Unauthorized”, as shown in the screenshot below.
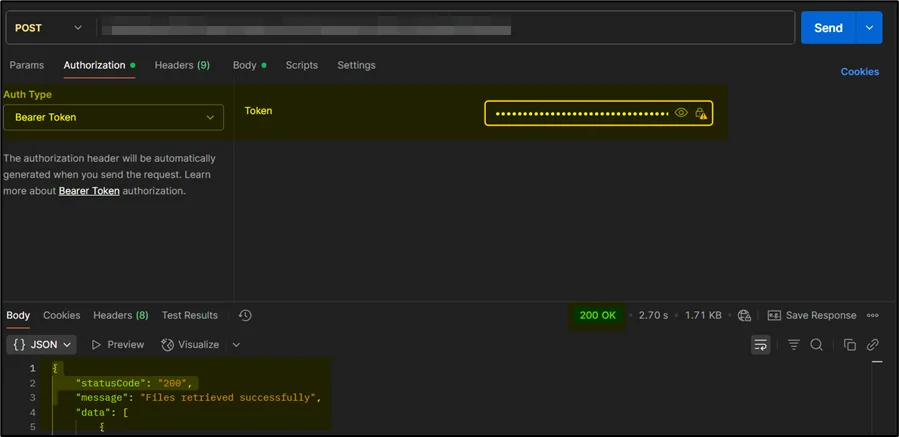
With Bearer Token: After adding the Amazon Cognito ID token as a Bearer Token in the Authorization header, the API successfully returns a 200 OK response with the expected data:
Advanced Features and Considerations
- Token Types and Usage:
- ID tokens: Used for authentication, contain user identity claims
- Access tokens: Used for authorization with custom OAuth 2.0 scopes
- Refresh tokens: Enable automatic token renewal for better user experience
- OAuth 2.0 Scopes: Fine-grained access control can be implemented using access tokens and scopes, allowing different levels of API access based on user roles or permissions.
- Multi-Factor Authentication: Enhanced security through optional MFA requirements, adding an extra layer of protection for sensitive operations.
- Federation Support: Integration with external identity providers through SAML or OpenID Connect, enabling single sign-on (SSO) capabilities.
- Token Caching: Amazon API Gateway caches token validation results for improved performance, reducing latency and Cognito API calls.
Conclusion
Implementing Amazon Cognito authorizers for Amazon API Gateway provides a scalable cost-effective API security solution. This integration simplifies authentication workflows while maintaining enterprise-grade security standards, enabling organizations to focus on delivering value rather than managing authentication infrastructure. Combining Amazon Cognito’s managed identity services with API Gateway’s powerful routing and authorization capabilities creates a secure foundation for modern API-driven applications. As cloud-native architectures evolve, this approach remains a cornerstone of AWS security best practices.
Drop a query if you have any questions regarding Amazon Cognito or Amazon API Gateway and we will get back to you quickly.
Empowering organizations to become ‘data driven’ enterprises with our Cloud experts.
- Reduced infrastructure costs
- Timely data-driven decisions
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. How should I handle the Authorization header in my API requests?
ANS: – Include the JWT token in the Authorization header. You can use either the “Bearer <token>” format or the token value directly. The Amazon API Gateway authorizer will extract and validate the token automatically.
2. What's the difference between ID tokens and access tokens in Amazon Cognito?
ANS: – ID tokens contain user identity information and are used for authentication, while access tokens are used for authorization and can include scopes for fine-grained access control.
3. Can I use Amazon Cognito authorizers with both REST and HTTP APIs?
ANS: – Yes, Amazon Cognito authorizers work with Amazon API Gateway REST APIs and HTTP APIs, though the configuration process may vary slightly between the two.

WRITTEN BY Sridhar Andavarapu
Sridhar Andavarapu is a Senior Research Associate at CloudThat, specializing in AWS, Python, SQL, data analytics, and Generative AI. He has extensive experience in building scalable data pipelines, interactive dashboards, and AI-driven analytics solutions that help businesses transform complex datasets into actionable insights. Passionate about emerging technologies, Sridhar actively researches and shares knowledge on AI, cloud analytics, and business intelligence. Through his work, he strives to bridge the gap between data and strategy, enabling enterprises to unlock the full potential of their analytics infrastructure.


 Login
Login


 September 2, 2025
September 2, 2025 PREV
PREV











Comments