|
Voiced by Amazon Polly |
1. Google Cloud KMS: An Overview
Data security is not just about storage; it’s about how securely that data is encrypted, managed, and accessed. Google Cloud Key Management Service (Cloud KMS) allows you to create, manage, rotate, and use cryptographic keys in a centralized way for your cloud applications and services.
Start Learning In-Demand Tech Skills with Expert-Led Training
- Industry-Authorized Curriculum
- Expert-led Training Sessions
2. What Problems Does Google Cloud KMS Solve?
- Data Privacy & Compliance: Helps meet data protection regulations (e.g., GDPR, HIPAA) by giving you full control over encryption keys.
- Centralized Key Management: Consolidates key lifecycle operations (creation, rotation, disabling, destruction) in one place.
- Secure Key Usage: Uses hardware security modules (HSMs) or software-based protection to perform cryptographic operations securely.
- Granular Access Control: Enforces strict IAM policies for who can use or manage keys.
- Auditable Key Usage: All actions are logged via Cloud Audit Logs for traceability.
3. Key Features of Google Cloud KMS
a) Symmetric & Asymmetric Key Support
- Symmetric keys: For encryption and decryption (AES-256).
- Asymmetric keys: For digital signatures and public-key encryption (RSA, EC).
b) Key Hierarchy
- KeyRing > Key > Key Version
This hierarchy allows for logical separation and versioning of keys.
c) Automatic Key Rotation
- Enables rotation policies (e.g., every 90 days) to reduce exposure from key compromise.
d) HSM-backed Protection
- Use Cloud HSM for FIPS 140-2 Level 3 compliance if required by regulatory frameworks.
e) IAM-based Access Control
- Fine-grained roles such as Cloud KMS CryptoKey Encrypter, Decrypter, Admin provide role-based access.
f) Audit Logging
- Integration with Cloud Audit Logs gives complete visibility into key usage and administrative actions.
4. How to Use Google Cloud KMS (via GCP Console)
Step 1: Create a Key Ring
- Go to Cloud Console > Security > Cryptographic Keys
- Click Create Key Ring
- Choose location (region or global)
- Give it a name, click Create
Step 2: Create a Key
- Click Create Key inside the key ring
- Choose symmetric or asymmetric key
- Select purpose: Encrypt/Decrypt or Sign/Verify
- Enable automatic rotation (optional)
- Click Create
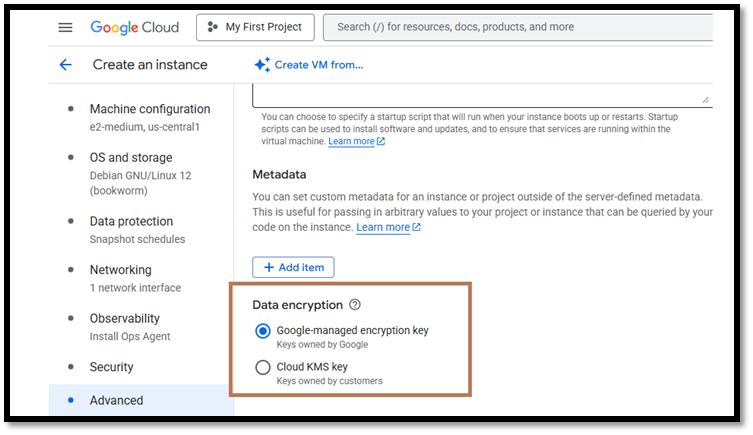
Step 3: Use the Key with a GCP Service
- When setting up Cloud Storage, BigQuery, or Compute Engine disk, choose “Customer-managed encryption key (CMEK)”
- Select your key ring and key from Cloud KMS
5. Best Practices for Using Cloud KMS
- Enable Key Rotation: Always enable automatic rotation to minimize exposure from key leaks.
- Audit All Access: Regularly review Cloud Audit Logs for any unauthorized usage patterns.
- Use IAM Roles Judiciously: Grant minimum necessary permissions to identities accessing KMS.
- Use Labels and Tags: Classify keys for auditing, billing, and lifecycle management.
6. Conclusion
Google Cloud KMS offers a secure, flexible, and fully managed way to handle encryption keys across your GCP infrastructure. Whatever data you’re protecting whether it is PII data, securing backups, or enabling trusted communication, Cloud KMS provides you with the tools and integrations needed for enterprise-grade key management.
By adopting Cloud KMS you not only enhance your security posture but also simplify compliance and auditing in the long term.
Upskill Your Teams with Enterprise-Ready Tech Training Programs
- Team-wide Customizable Programs
- Measurable Business Outcomes
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. Can I use Google Cloud KMS outside of GCP?
ANS: – Yes. You can call the KMS API from external applications or on-prem workloads to encrypt/decrypt data securely.
2. Is Cloud KMS suitable for regulatory compliance like HIPAA or PCI?
ANS: – Yes. Cloud KMS (and Cloud HSM) can help meet strict compliance requirements. Always consult your auditor and use audit logs.
3. What happens when I disable or destroy a key?
ANS: – Once destroyed, a key version cannot be used ever again. Disabling prevents its use until re-enabled — useful for temporary lockouts.

WRITTEN BY Abhijit Dilip Powar
Abhijit Dilip Powar is a Senior Vertical Head at CloudThat Technologies Private Limited, specializing in Cloud Architecting and Security. With 21 years of experience in industry and academics, he has trained over 10K professionals/students to upskill in Cloud Architecting and Security. Known for delivery skills customization as per the participants attending the trainings, he brings deep technical knowledge and practical application into every learning experience. Abhijit's passion for teaching reflects in his unique approach to learning and development.


 Login
Login


 September 10, 2025
September 10, 2025 PREV
PREV











Comments