|
Voiced by Amazon Polly |
Overview
Managing patch compliance across multiple AWS accounts is a growing challenge in large-scale cloud environments. This blog explores how to centrally manage and automate EC2 patching across AWS accounts using AWS Systems Manager (SSM) and Terraform.
By adopting a centralized patching architecture, organizations can:
- Enforce consistent security policies from a master account
- Share AWS-managed patch baselines across child accounts.
- Automate patch deployment via SSM Associations and Maintenance of Windows
- Maintain compliance visibility across accounts using native AWS tools
- Scale seamlessly with modular, Terraform-based infrastructure
This guide walks through the prerequisites, AWS IAM configuration, tagging strategy, terraform implementation steps, and architecture design needed to implement this solution. Whether you’re a security engineer or a DevOps professional, this approach provides a scalable, secure, and auditable way to manage patching across AWS environments.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
Introduction
As organizations scale their AWS infrastructure, managing consistent patching policies across multiple accounts becomes crucial for security and compliance. AWS Systems Manager (SSM) simplifies patching automation and allows for the sharing of patching baselines from a central account to multiple child accounts.
In this blog, we walk through how to implement cross-account SSM patching using Terraform, enabling centralized control while allowing distributed execution across accounts.
Why We Are Doing This?
- Centralized Control: Manage and enforce patch compliance policies from a single security or DevOps account.
- Scalability: Easily extend the patching solution across dozens or hundreds of AWS accounts without manual setup.
- Security and Compliance: Ensure consistent patching of vulnerabilities to meet regulatory standards (e.g., CIS, HIPAA).
- Cost Optimization: Avoid redundant configuration and tool sprawl using AWS-native features like SSM.
- Audit Readiness: Maintain visibility and traceability of patching operations across your organization.
Prerequisites
Before getting started, ensure you have the following:
- Terraform (>=1.0.0) installed on your local machine
- AWS CLI configured for both central (master) and child accounts
- IAM permissions to create and manage SSM and Amazon EC2 resources
- Tags applied to Amazon EC2 instances to group them for patching (e.g., Patch Group)
- A proper role in child accounts allowing SSM to run patching commands
- Cross-account trust relationship configured if assuming roles between accounts
Terraform Checklist
Before you begin writing infrastructure code, consider the following:
- Understand the Use Case
- Define the objective (e.g., centralized patching using AWS-managed patch baselines)
- Identify participating AWS accounts and their roles (master and child)
- Identify Required Services
- AWS Systems Manager (SSM)
- AWS Identity and Access Management (IAM)
- Amazon EC2 (for tagging and patching targets)
- Design the Architecture
- Master account uses AWS default patch baseline
- Child accounts associate Amazon EC2 tags and automate patching
- Define AWS IAM Requirements
- AWS Systems Manager (SSM) execution role for patching in child accounts
- Role assumption policies between accounts
- Write and Organize Terraform Code
- Separate files/modules for patch group and automation
- Use variables.tf, main.tf, and outputs.tf for modular structure
- Include tagging, versioning, and logging where possible
- Testing & Validation
- Ensure Amazon EC2 instances are tagged correctly
- Simulate patch execution via manual association run or maintenance window
|
1 2 3 4 5 6 7 8 9 10 11 12 |
Architecture Diagram [ Master Account] | |---> Reference AWS Default Patch Baseline | [ Child Accounts] |---> Use AWS Default Patch Baseline |---> Tag EC2 Instances |---> Automate Patching with AWS Systems Manager (SSM) Association / Maintenance Window |
Step-by-Step Implementation
Step 1: Use Default Patch Baseline in Master Account


Step 2: Use Patch Baseline in Child Account

Patch baselines for Child account created same as Master account

This ensures all Amazon EC2 instances tagged with Patch Group = Child-Prod-Group are patched automatically every week.
Step 3 (Optional): Automate Patching with Maintenance Window

Once you run the terraform code, the Configuration of the Master Account SSM looks like this:

Target as selected:

After the AWS Systems Manager (SSM) Patching is done, it looks like this in the Child Account
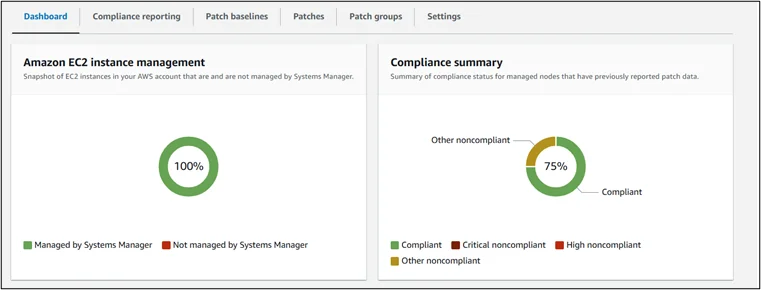
Benefits

Use Case
A central AWS account (Security or DevOps account) maintains patching standards and compliance requirements. Multiple child accounts host workloads that must adhere to the same patching standards.
The goal:
- Define and manage patch baselines centrally
- Automate patch application via SSM Associations and optionally Maintenance Windows Conclusion
Cross-account SSM patching helps enforce uniform security policies at scale. With Terraform, you can automate the setup of patch baselines and patch enforcement through SSM Associations or Maintenance Windows. This approach ensures security compliance and reduces manual overhead in managing multi-account environments.
Conclusion
By leveraging AWS-native services like AWS Systems Manager, Resource Access Manager, and AWS IAM roles, teams can enforce uniform patch baselines from a single account and ensure consistent operations across multiple child accounts. This improves security and audit readiness and reduces manual overhead, enabling DevOps and security teams to focus on higher-value tasks.
Drop a query if you have any questions regarding SSM patching and we will get back to you quickly.
Empowering organizations to become ‘data driven’ enterprises with our Cloud experts.
- Reduced infrastructure costs
- Timely data-driven decisions
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. What is cross-account SSM patching?
ANS: – Cross-account SSM patching refers to using AWS Systems Manager (SSM) to automate the patching of Amazon EC2 instances across multiple AWS accounts from a centralized (master) account. It shares patch baselines and enables centralized control with distributed execution.
2. Why should I centralize patch management?
ANS: – Centralizing patch management provides better governance, enforces consistent security policies, reduces duplication of effort, and simplifies auditing. It also helps in scaling patching practices across multiple AWS accounts securely and efficiently.
WRITTEN BY Abhiram Konidena


 Login
Login


 June 19, 2025
June 19, 2025 PREV
PREV











Comments