|
Voiced by Amazon Polly |
Introduction
As enterprises scale their Kubernetes and cloud-native platforms, the complexity of governance grows exponentially. Teams need guardrails for security, compliance, and operational consistency, without slowing developer velocity. Traditional manual reviews and ad-hoc policies cannot keep up with the dynamic nature of cloud-native workloads.
This is where Policy-as-Code (PaC) comes in. By codifying security and compliance rules into version-controlled, testable policies, enterprises can shift governance left and enforce it automatically in Kubernetes clusters.
In this blog, we explore how OPA (Open Policy Agent) and Kyverno enable enterprise-grade policy enforcement, integrate seamlessly with GitOps pipelines, and provide scalable governance across multi-cluster Kubernetes environments.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
Architecture Overview
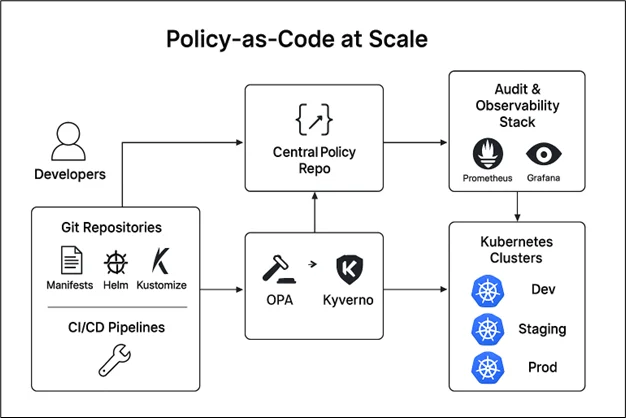
Architecture Explanation:
The architecture demonstrates a multi-cluster Kubernetes governance model powered by OPA Gatekeeper and Kyverno.
- Developers commit manifests (YAML, Helm, Kustomize) into Git repositories.
- CI/CD pipelines run policy checks using OPA/Kyverno policies before merging changes.
- ArgoCD continuously reconciles manifests into target clusters.
- OPA Gatekeeper validates resources against enterprise guardrails (e.g., no privileged containers, restricted namespaces).
- Kyverno applies mutation and generation policies (e.g., auto-inject labels, enforce resource limits).
- Audit & Observability Stack (Prometheus, Grafana, Loki) captures policy violations and generates compliance reports.
- Central Policy Repo is the single source of truth for all governance rules.
This ensures developers move fast while platform teams maintain enterprise-wide compliance.
The Shift: From Manual Reviews to Policy-as-Code
Traditional governance relies on ticket-based approvals, security scans, or periodic audits. But in Kubernetes, resources are continuously deployed across environments, and manual checks don’t scale.
Policy-as-Code shifts governance into the pipeline: policies live in Git, are peer-reviewed, tested, and enforced automatically at deploy time. This model enables continuous compliance rather than reactive auditing.
Core Pillars of Policy-as-Code at Scale
Declarative Policies in Git
- Policies stored as code in Git repos.
- Versioned, peer-reviewed, and auditable.
Multi-Layer Enforcement
- Pre-merge checks in CI pipelines.
- Admission control via OPA/Kyverno in clusters.
Separation of Concerns
- Developers focus on business logic.
- Platform/security teams own policy repos.
Continuous Compliance
- Violations detected and remediated in real-time.
- Automated dashboards for auditors and stakeholders.
Challenges in Policy-as-Code Implementation
- Policy Sprawl
Multiple teams are writing conflicting policies.
Solution: Centralize ownership with a governance team; adopt reusable policy libraries. - Balancing Security & Developer Experience
Overly restrictive policies hinder velocity.
Solution: Apply progressive enforcement, warn first, block later. - Cross-Cluster Consistency
Ensuring the same guardrails across dev, staging, and prod.
Solution: Sync policies using GitOps into all clusters. - Observability of Policy Violations
Hard to track violations at scale.
Solution: Integrate with Prometheus/Grafana dashboards for visibility.
Best Practices for Policy-as-Code in Kubernetes
- Adopt a Dedicated Policy Repo
Keep policies separate from application code. Enables independent lifecycles. - Test Policies in CI/CD
Run conformance checks before merging manifests. - Enable Progressive Enforcement
Start with audit-only mode, then move to deny-by-default. - Combine OPA & Kyverno
OPA is used for complex validation, and Kyverno is used for user-friendly mutation/generation. - Provide Developer Feedback Loops
Make violation messages clear and actionable. - Audit & Report Regularly
Provide compliance dashboards to leadership and auditors.
Outcomes of Policy-as-Code
- 80% reduction in policy violations, detected pre-merge, not in production.
- Faster compliance audits, and all policies are versioned and traceable in Git.
- Consistent governance across 10+ clusters with zero drift.
- Improved developer trust and clear guardrails instead of ad-hoc rejections.
- Regulatory readiness, policies mapped directly to frameworks (CIS, PCI-DSS, HIPAA).
Conclusion
In modern DevOps, governance cannot be an afterthought. Policy-as-Code with OPA and Kyverno ensures enterprises can scale Kubernetes securely while empowering developers to innovate.
By shifting compliance left, codifying guardrails in Git, and enforcing them continuously across clusters, organizations achieve secure velocity, delivering faster without compromising trust or compliance.
As cloud-native adoption accelerates, Policy-as-Code will be a non-negotiable pillar of enterprise DevOps strategies.
Drop a query if you have any questions regarding OPA and we will get back to you quickly.
Empowering organizations to become ‘data driven’ enterprises with our Cloud experts.
- Reduced infrastructure costs
- Timely data-driven decisions
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. Do I need both OPA and Kyverno?
ANS: – Not necessarily. OPA is powerful for complex Rego-based validations, while Kyverno is more Kubernetes-native and user-friendly. Many enterprises use them together.
2. Can policies be applied across clouds?
ANS: – Yes. With GitOps, the same policies can be synced into Amazon EKS, GKE, and AKS clusters.
3. What happens when policies block deployments?
ANS: – Deployments fail fast with actionable violation messages, preventing misconfigurations from reaching production.

WRITTEN BY Sourabh Murgod
Sourabh Murgod works as a Research Associate at CloudThat, focusing on AWS, Kubernetes, and DevOps engineering. He is passionate about designing scalable cloud architectures, automating infrastructure, and optimizing production workloads.


 Login
Login


 September 23, 2025
September 23, 2025 PREV
PREV











Comments