|
Voiced by Amazon Polly |
Overview
In today’s cloud-centric world, managing permissions and ensuring security across multiple AWS accounts can be daunting. AWS Organizations provides a powerful feature called Service Control Policies (SCPs) that allows you to manage and enforce permissions across your entire organization centrally. In this blog post, we’ll explore how to implement SCPs to control access to AWS services and resources across different accounts within your AWS Organization.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
Service Control Policies (SCPs)
Service Control Policies (SCPs) are a type of policy that you can use to manage permissions in your AWS Organization. SCPs allow you to set permission guardrails, defining the maximum permissions that AWS IAM users and roles in your organization can have. It’s important to note that SCPs do not grant permissions themselves; instead, they limit the permissions that identity-based and resource-based policies can grant.
Setting Up AWS Organizations
Before you can implement SCPs, you need to set up AWS Organizations. AWS Organizations allows you to consolidate multiple AWS accounts into a single organization that you can centrally manage. Here’s how to get started:
- Create an AWS Organization: If you haven’t already, create an AWS Organization from the AWS Management Console.
- Enable All Features: Ensure your organization has all features enabled, as SCPs are only available in organizations with all features enabled.
- Create Organizational Units (OUs): Organize your accounts into OUs based on your business structure or security requirements.
Creating and Attaching SCPs
Once your AWS Organization is set up, you can create and attach SCPs to your OUs or individual accounts. Follow these steps:
Step 1: In AWS Console, Search “AWS Organization”

Step 2: Go into policies and click on “Create policy”

Step 3: Give a name to the policy and write a policy description.
Step 4: Write a policy in the given section.

Define Your SCP: Write the SCP in JSON format. SCPs use the same syntax as AWS IAM policies. Here’s an example SCP that denies access to specific AWS regions:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Deny", "Action": "*", "Resource": "*", "Condition": { "StringNotEquals": { "aws:RequestedRegion": [ "ap-south-1", "ap-south-2" ] } } } ] } |
This will allow resource creation only in the Mumbai region. This policy stops actions in any region except for ap-south-1 and ap-south-2. It will be denied if you try to do something outside of these two regions.
Step 5: After writing a policy, click on Create Policy, and then you can see as below:

Step 6: Recheck and verify before applying it on the account level

Attach the SCP: Attach the SCP to the appropriate OU or account. You can do this from the AWS Management Console.
Step 7: As shown below, you can apply policies at the targeted account and root levels. Applying on root will automatically apply on all the accounts that come under it.
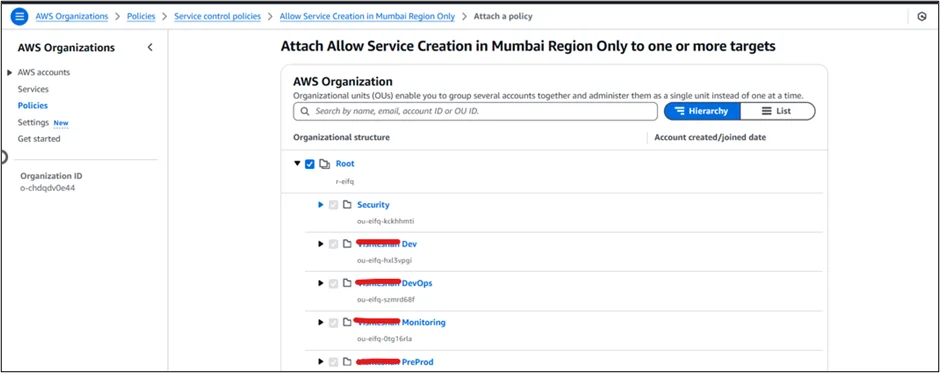
Step 8: Apply the policy successfully.
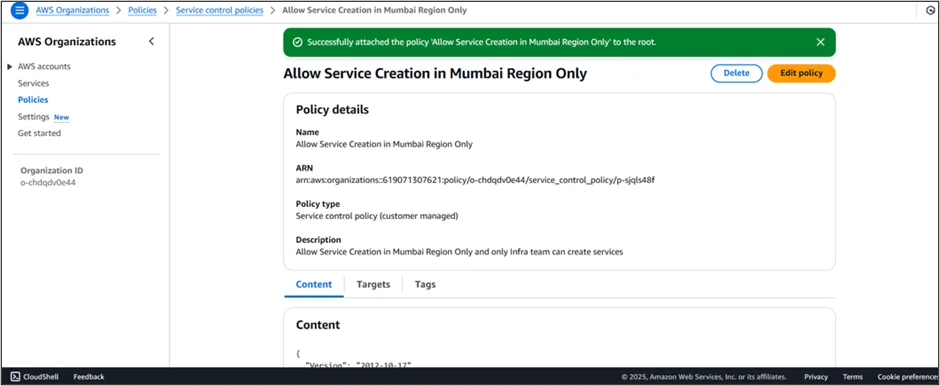
Testing and Monitoring SCPs
It’s crucial to thoroughly test your SCPs before applying them broadly. AWS recommends creating a test OU and moving accounts into it one at a time to ensure that the SCPs do not inadvertently block necessary permissions. Additionally, you can use AWS CloudTrail and AWS IAM Access Analyzer to monitor and analyze the effects of your SCPs.
Best Practices for SCPs
Here are some best practices to keep in mind when implementing SCPs:
- Start with a Deny List: Begin with a deny list policy strategy to block unwanted actions and services.
- Use Service Last Accessed Data: Utilize service last accessed data to refine your SCPs and ensure they only restrict necessary services.
- Regularly Review and Update SCPs: Periodically review and update your SCPs to adapt to changing business and security requirements.
Conclusion
Following the steps outlined in this blog post, you can effectively control access to AWS services and resources, helping your organization stay within its access control guidelines.
Drop a query if you have any questions regarding Service Control Policies and we will get back to you quickly.
Empowering organizations to become ‘data driven’ enterprises with our Cloud experts.
- Reduced infrastructure costs
- Timely data-driven decisions
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.
FAQs
1. Do SCPs grant permissions to users or roles?
ANS: – No, SCPs do not grant permissions themselves. They only limit the permissions that other policies can grant. If permission is not allowed by the SCP, it cannot be granted by any identity-based or resource-based policy.
2. Can I apply an SCP to a single AWS account?
ANS: – Yes, you can attach an SCP to an individual AWS account or an Organizational Unit (OU) with multiple accounts. SCPs applied to an OU will affect all accounts within that OU.
WRITTEN BY Runal Paliwal


 Login
Login


 March 18, 2025
March 18, 2025 PREV
PREV










Comments