|
Voiced by Amazon Polly |
In the world of Linux, permissions form the foundation of system security. Every file and directory in a Linux system has defined permissions that determine who can read, write or execute them.
While regular permissions (read r, write w, execute x) are crucial for daily operations, special permissions, namely SUID, SGID and Sticky Bit, add an additional layer of control and flexibility to file execution and shared directories.
Understanding these permissions is essential for system administrators, DevOps engineers and security professionals who manage Linux-based infrastructure or applications.
Freedom Month Sale — Upgrade Your Skills, Save Big!
- Up to 80% OFF AWS Courses
- Up to 30% OFF Microsoft Certs
- Ends August 31
Basic File Permissions
Before diving into special permissions, let’s recall the basics.
Every file in Linux has three sets of permissions:
- Owner (User)
- Group
- Others
Each can have:
- r (read) — ability to view contents
- w (write) — ability to modify contents
- x (execute) — ability to run the file
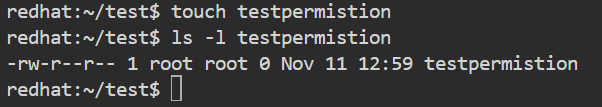
This means:
- User: read, write, Group: read, Others: read
Understanding Linux Special Permissions
Special permissions extend the traditional rwx system with three additional attributes:
- SUID (Set User ID)
- SGID (Set Group ID)
- Sticky Bit
They modify how processes and files behave when executed or accessed by other users. Let’s understand each one in detail with real examples.
- SUID – Set User ID
When a file with the SUID bit set is executed, the process runs as the owner of the file, not as the user who executed it. This is especially useful when normal users need temporary access to perform administrative actions without becoming root.
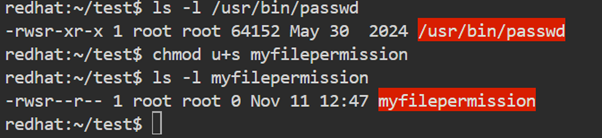
Real-World Example: /usr/bin/passwd
When you change your password using the passwd command, it needs to modify the /etc/shadow file, which only root can access. Even though you are a normal user, the passwd command works because it has the SUID bit set.
Here:
- Owner: root, Permission: rws → SUID set, any user can execute it as root temporarily
- SGID – Set Group ID
The SGID bit behaves differently for files and directories:
- For files: The executed file runs with the group ownership of the file, not the user’s group.
- For directories: Any file created inside inherits the directory’s group ownership.
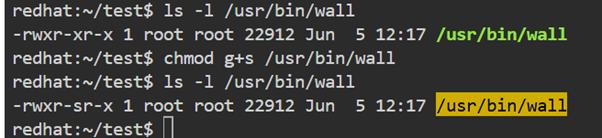
/usr/bin/wall allows users to broadcast messages to all users, but executes under the root group, not under the user’s group.
SGID on directories is extremely useful for collaborative environments.
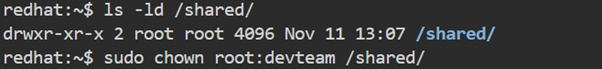
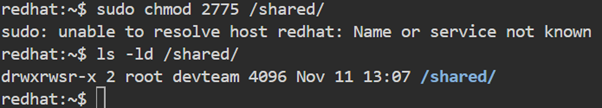
Now, when any developer from the devteam group creates files inside /shared, those files will inherit the devteam group, ensuring consistent permissions across the team.
- Sticky Bit
The Sticky Bit applies only to directories.
It ensures that only the file’s owner (or root) can delete or rename the files inside that directory, even if others have written permissions.
Common Example: /tmp Directory/tmp is world-writable – every user can create temporary files there.
Without the Sticky Bit, users could delete others’ files, causing chaos.
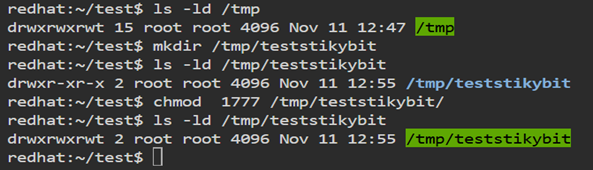
Now, create files as two different users:
- User A creates file1 inside teststickybit
- User B tries to delete file1 – not allowed
This demonstrates that the Sticky Bit protects each user’s files within a shared, writable directory.
Security Best Practices
- Avoid setting SUID/SGID on custom scripts.
- Restrict SUID binaries.
- Use SGID only for group collaboration directories.
- Always ensure Sticky Bit is set on /tmp and /var/tmp.
- Audit file permissions regularly.
If you want more information, you can try browsing the Official Red Hat Certification catalog and their subscription plans for more information regarding the process.
Linux Security Insights
Linux special permissions such as SUID, SGID and Sticky Bit may seem like minor additions to the rwx model, but they play a vital role in secure system administration. They enable controlled privilege escalation, safe group collaboration and protection in shared environments.
For DevOps engineers and administrators, mastering these permissions is key to balancing functionality with security, especially in shared or automated environments like CI/CD pipelines, shared Docker volumes or multi-user Linux systems.
So next time you list file permissions and see an ‘s’ or ‘t’, you’ll know exactly what magic is happening behind the scenes.
Freedom Month Sale — Discounts That Set You Free!
- Up to 80% OFF AWS Courses
- Up to 30% OFF Microsoft Certs
- Ends August 31
About CloudThat
CloudThat is an award-winning company and the first in India to offer cloud training and consulting services worldwide. As a Microsoft Solutions Partner, AWS Advanced Tier Training Partner, and Google Cloud Platform Partner, CloudThat has empowered over 850,000 professionals through 600+ cloud certifications winning global recognition for its training excellence including 20 MCT Trainers in Microsoft’s Global Top 100 and an impressive 12 awards in the last 8 years. CloudThat specializes in Cloud Migration, Data Platforms, DevOps, IoT, and cutting-edge technologies like Gen AI & AI/ML. It has delivered over 500 consulting projects for 250+ organizations in 30+ countries as it continues to empower professionals and enterprises to thrive in the digital-first world.

WRITTEN BY Martuj Nadaf
Martuj Nadaf is a Subject Matter Expert at CloudThat, specializing in DevOps Tools and multi-cloud. With 14 years of experience in training and industry, he has trained over 2000+ professionals/students to upskill in Hardware, Networking, Windows, Linux, DevOps, Docker, Kubernetes, Monitoring tools, Multi-cloud globally. Known for explaining complex technical concepts in a simple and understandable manner, hands-on teaching and industry insights, he brings deep technical knowledge and practical application into every learning experience. Martuj's passion for exploring new technologies reflects in his unique approach to learning and development.


 Login
Login


 November 25, 2025
November 25, 2025 PREV
PREV










Comments