Office 365
Office 365 is a great offering by Microsoft which helps its users manage their environment and configure a lot of security measures to safeguard your organization.
But one might have a lot of questions. Where to start? What all is necessary for my organization? What all is already enabled by default?
The answer to all of these questions is the ORCA report. ORCA stands for Office 365 ATP Recommended Configuration Analyzer. Office 365 Advanced Threat Protection (name has now changed to Microsoft Defender for Office 365) is an add-on service for Office 365 to protect users against malicious threats by email, URL, and collaboration tools. You would need to have the Microsoft Defender for Office 365 Plan 1 or Plan 2 to use this functionality.
So how can you get this report? You can follow the below steps to generate your organization’s ORCA report.
- Launch a PowerShell window on your system (make sure to run it as an administrator).
- Then install the ORCA PowerShell Module:
Install-Module -Name ORCA
- After it has installed, you would have to connect to Exchange Online with PowerShell. Use the below command for that:
Connect-ExchangeOnline
- You would be prompted to sign-in and complete the MFA protection.
- After the sign is completed and you are back on the PowerShell window run the below command to generate the ORCA report:
Get-ORCAReport
- It would generate an HTML file (location would be shown in the PowerShell window).
After you open the file, you would see this:
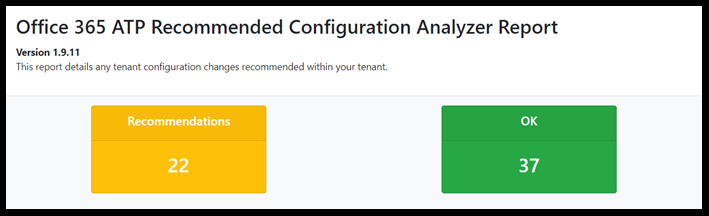

You would see a summary listing out all the possible categories with the count of recommendations and the settings which are correctly marked in yellow and green respectively.
Anti-Spam policies would include configurations like removing all email addresses and domains from the whitelisted list, Spam notifications management, Setting outbound spam filter policy settings, and many more. For example, here I have a recommendation that asks me to enable end-user spam notifications and set the frequency to 3.

The current value for this setting is ‘False’. There are 3 setting configuration options namely Default, Standard, and Strict. Microsoft recommends using the Standard and Strict configurations as per your requirement.
Coming back to the recommendation, how can you rectify/configure this setting?
To enable the anti-spam policies, I would need to go to the Office365 security and compliance center. From that portal, you would need to go to policies and then Anti-Spam to edit the default policy or even making a new policy from scratch.
You can follow the below steps to enable the recommendation in the report:
- Open the Anti-spam policy page(https://protection.office.com/antispam) and open the default spam filter policy.
Click on ‘End-user spam notifications’ and in the wizard, which opens enabled the setting and set it for 3 days.
We can configure another recommendation on the same page.

This configuration recommends us to set a limit for outbound emails. This can be configured in the Outbound spam filter policy. Make sure to do the following changes in it.
- Turn on “Notify specific people if a sender is blocked due to sending outbound spam” in the Default policy.
- Add an email address (preferably security admin or someone responsible for managing this) as a recipient for notifications when a user is blocked. (Disabled by default)
- In recipient limits, changing the external hourly limit to 500(from 0), internal hourly limit to 1000(from 0), and daily limit to 1000(from 0) and change the action when a user exceeds the specified limits to “Restrict the user from sending email” (from Restrict the user from sending day for the following day).
(Note: The limit of 1000 and 500 are as per Standard configurations if you want to have Stricter measures you can set it to 800 and 400 respectively).
The next section in the summary was Advanced Threat protection policies which include Safe Attachments, Safe links configuration for all your recipient domains/users from both external and internal threat.
The other recommendations in my report included DKIM and malware filter policy.
DKIM recommendations involve configuring DKIM signing which helps to protect the authenticity of your messages in transit and can assist with the deliverability of your email messages.
The malware filter policy involves the creation/modification of Anti-Malware policies which are used to manage notifications to senders and handling of the malware coming into the organization.
You can find the Microsoft recommended settings for Exchange online protection and Office 365 Advanced threat protection (Microsoft Defender for Office 365) in the below Microsoft documentation:
ORCA report recommendations would be a great help for you and your organization. For any queries or suggestions please feel free to drop a comment I would be really happy to read and respond to it.
Also, if you are an organization that needs help with managing its Office 365 environment and making use of your licenses efficiently to get hold of all the security features provided feel free to drop an email to sales@cloudthat.in and we can connect and help you out.
Get your new hires billable within 1-60 days. Experience our Capability Development Framework today.
- Cloud Training
- Customized Training
- Experiential Learning

WRITTEN BY CloudThat


 Login
Login


 December 24, 2020
December 24, 2020 PREV
PREV










Swastika
Mar 8, 2021
Thanks for posting. Helpful